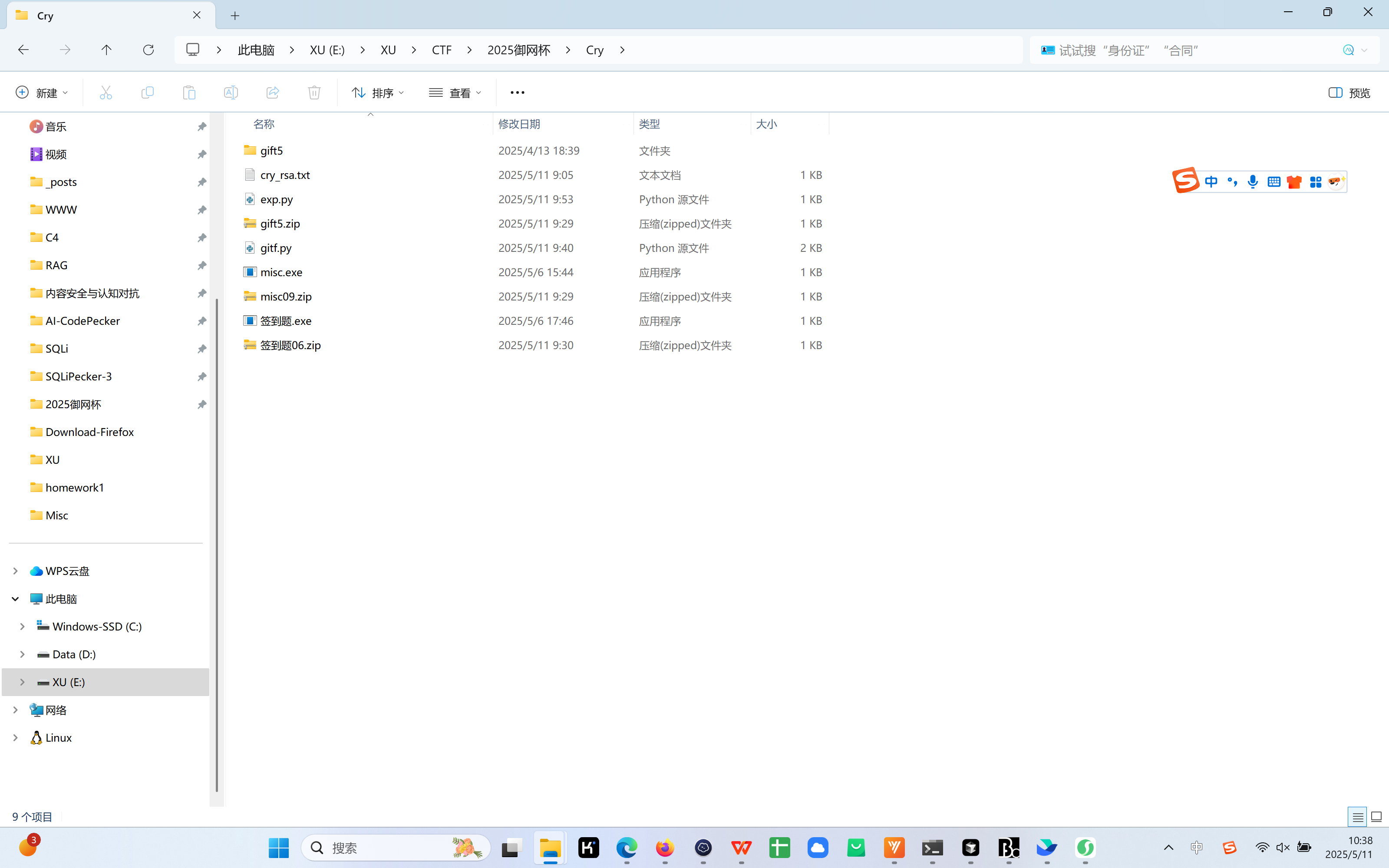
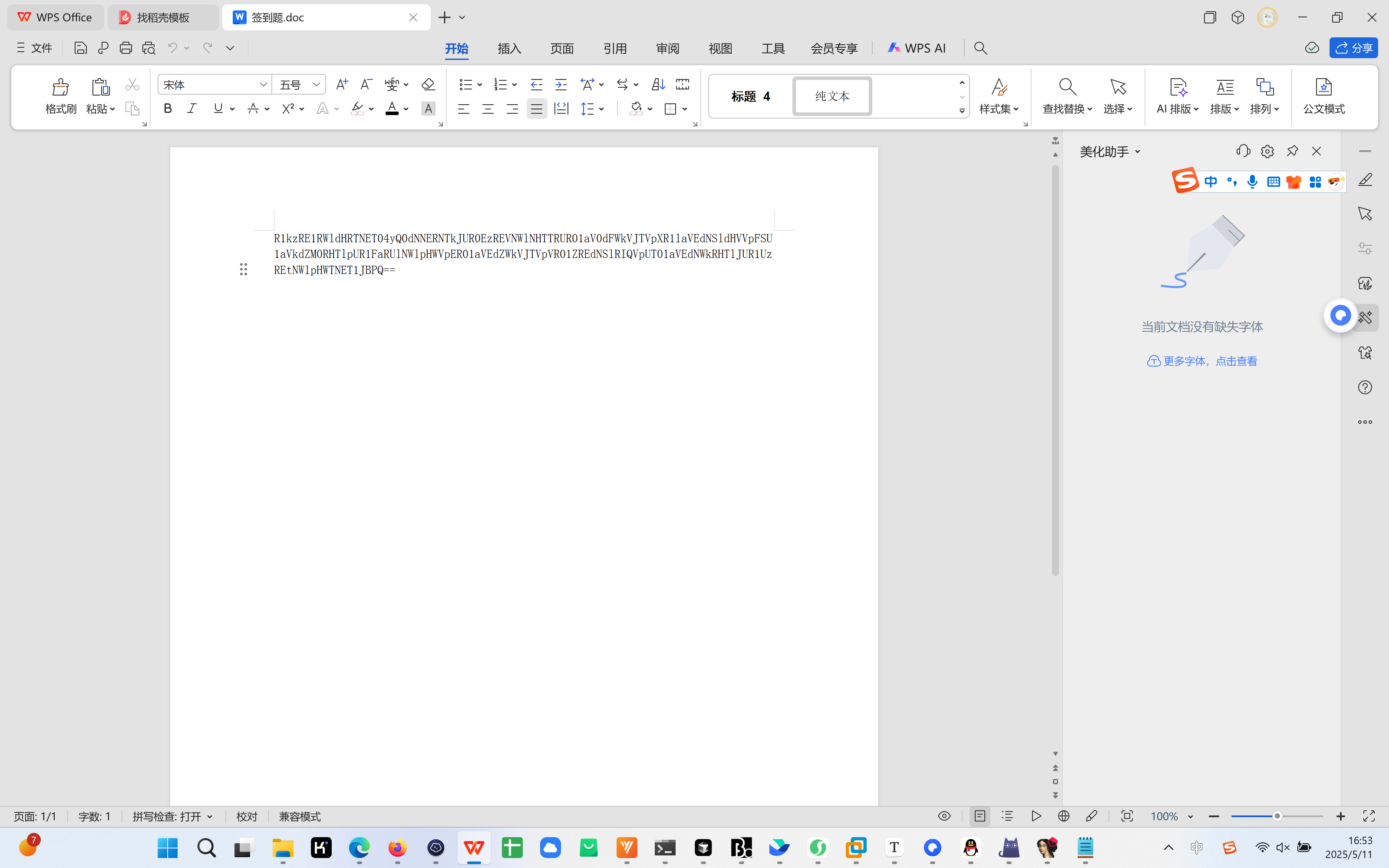
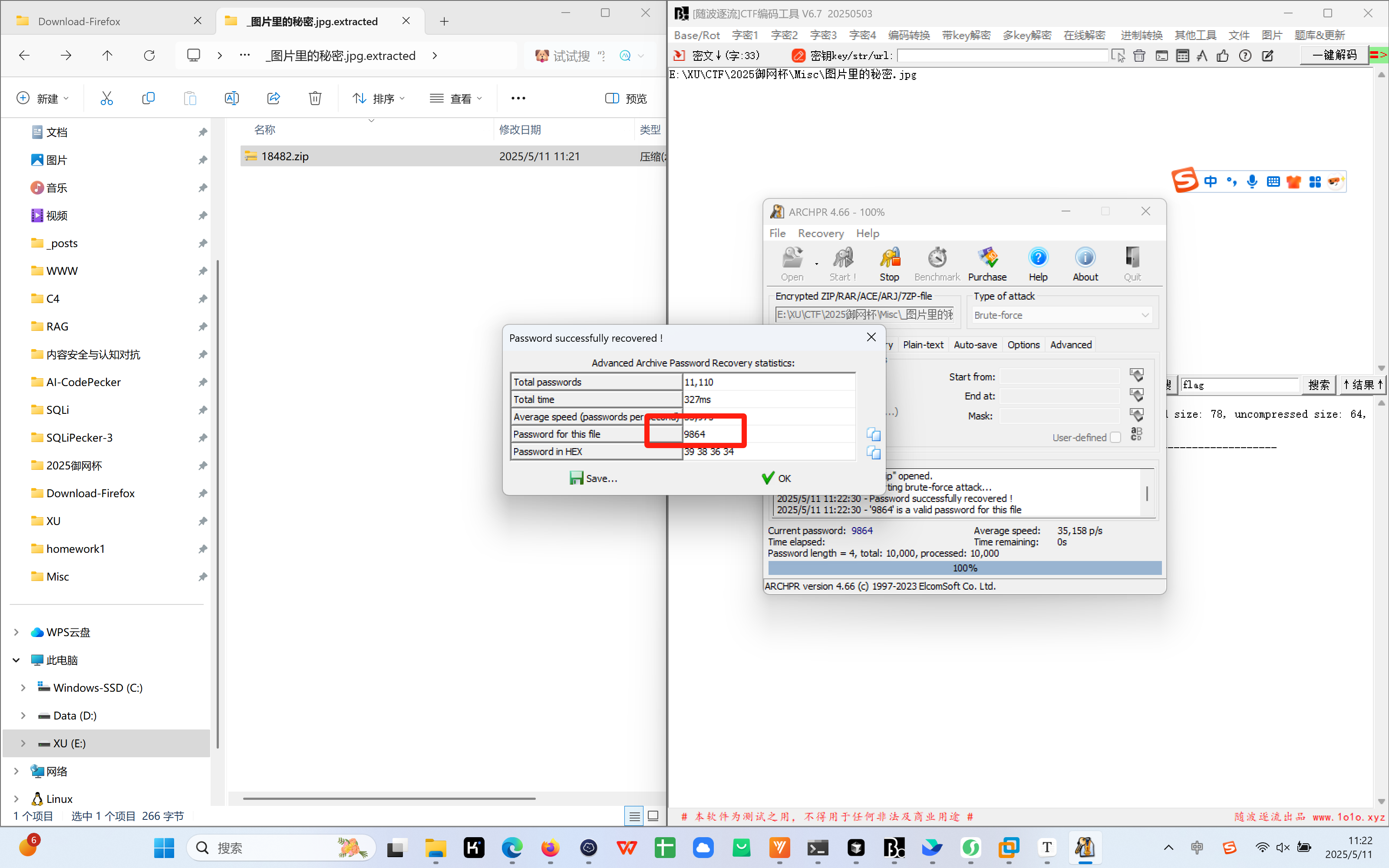
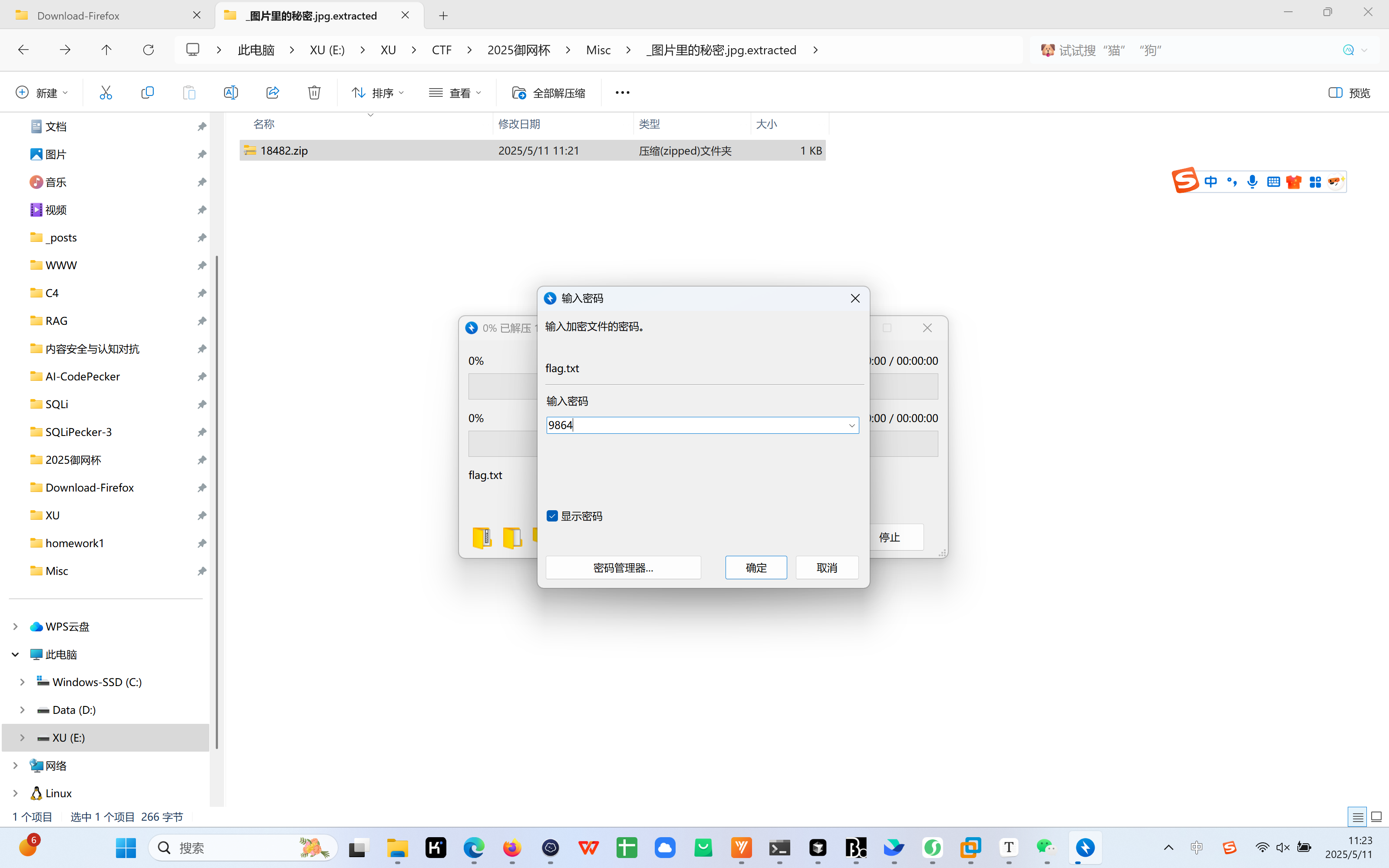
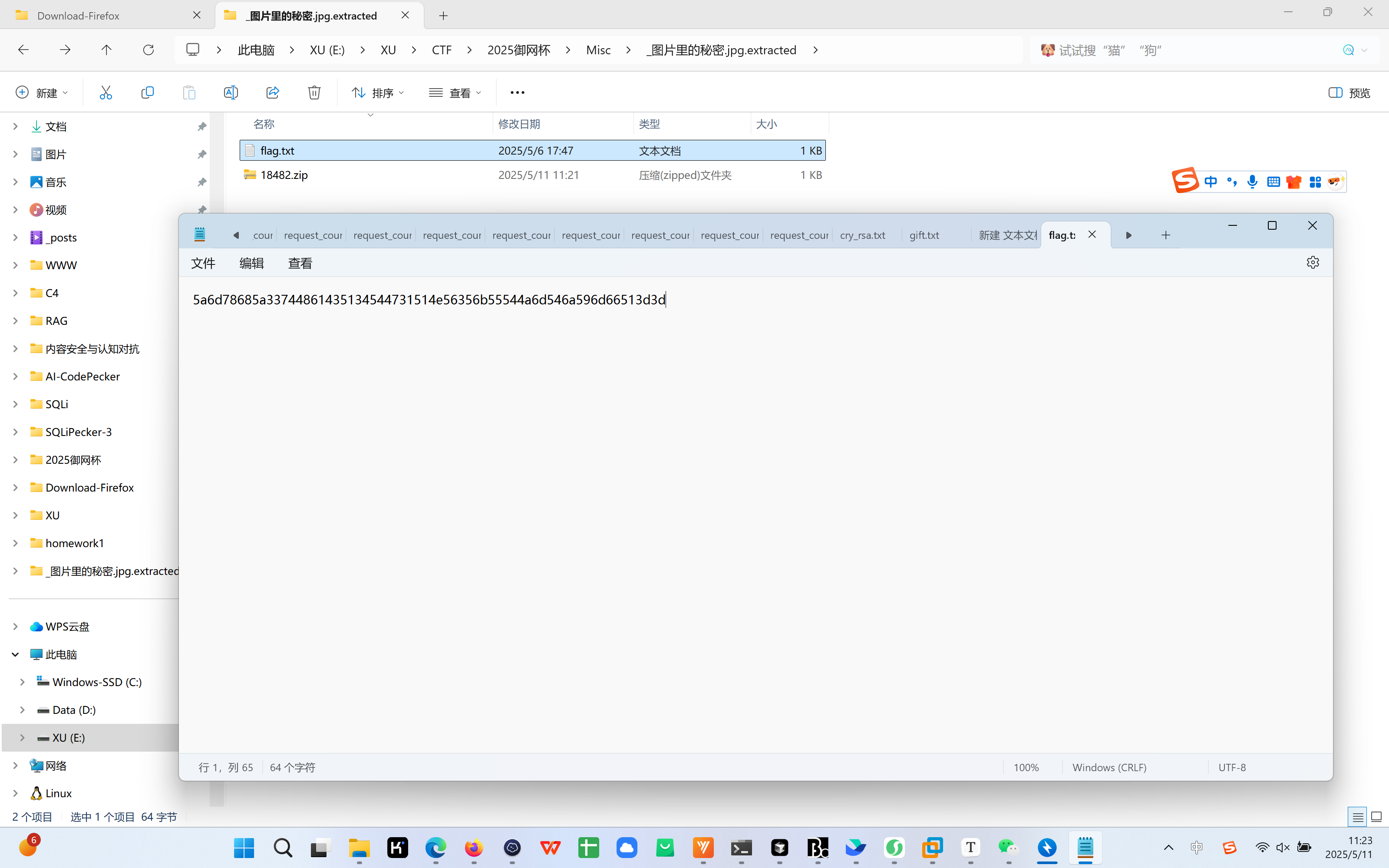
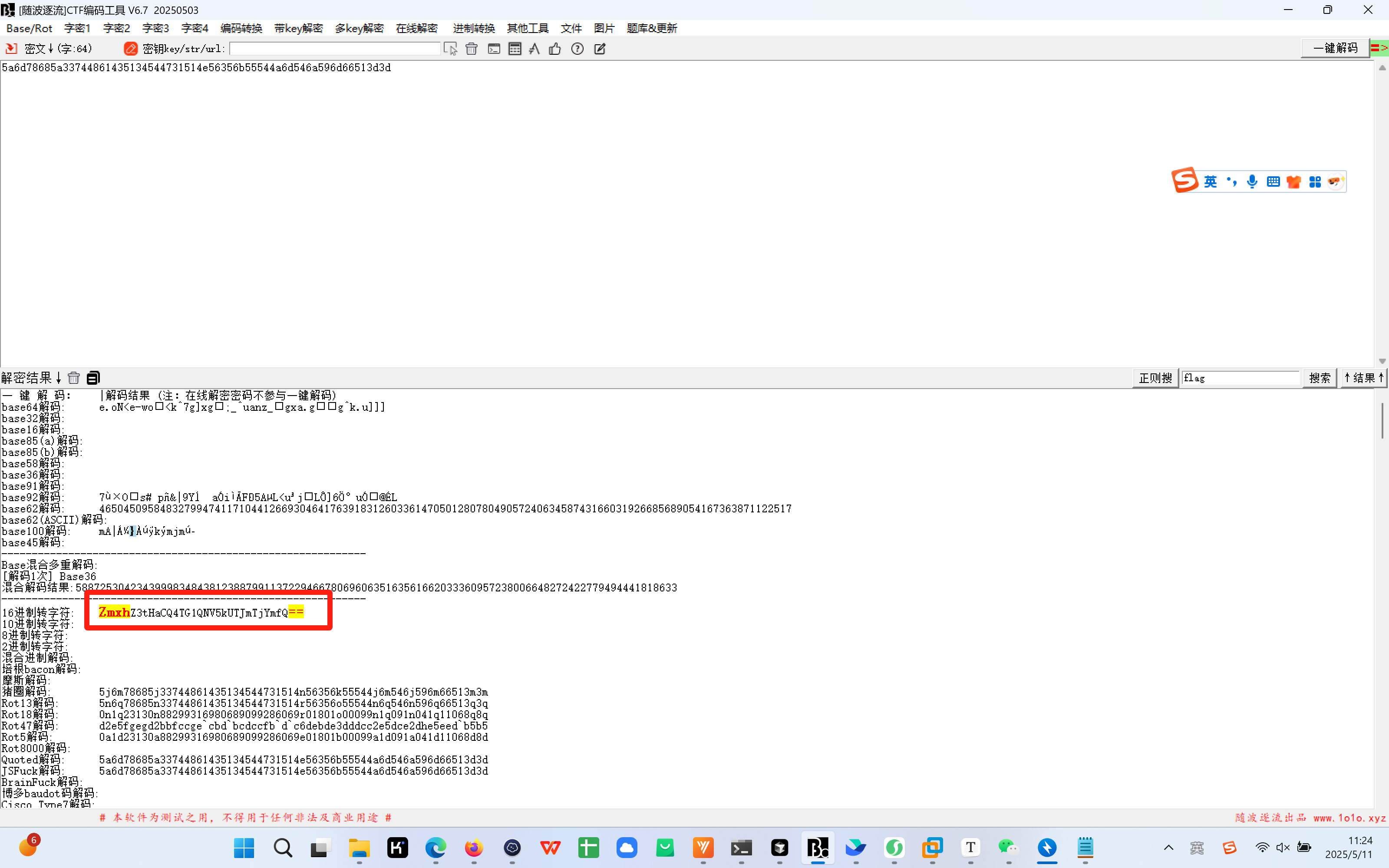
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
| from sage.all import PolynomialRing, QQ
from scipy.optimize import least_squares
import numpy as np
def solve_flag():
R = PolynomialRing(QQ, 38, 'x')
x = R.gens()
known = {
x[0]: 102,
x[1]: 108,
x[2]: 97,
x[3]: 103,
x[4]: 123,
x[37]: 125
}
eqs = [
x0 * x16 + x10 * x18 + 2 * (x11 * x25) + 5 * (x13 * x25) - 9 * (x13 * x32) - 8 * (x15 * x29) + 8 * (x17 * x28) + 7 * (x19 * x29) - 5 * (x19 * x30) - 7 * (x19 * x9) - 4 * x20 * x20 + 7 * (x22 * x23) - 5 * (x23 * x8) - 8 * (x29 * x5) - 7 * x31 + 7 * (x32 * x9) + 10 * (x33 * x4) + 8 * x5 * x5 - 5 * x8 * x8 - 16191 ,
-9 * (x1 * x15) - 2 * (x10 * x18) + 9 * (x11 * x18) - 6 * (x12 * x16) - x14 * x15 - 3 * (x15 * x18) - 9 * (x16 * x8) + 10 * (x17 * x23) + 4 * (x17 * x5) - 2 * (x2 * x22) - 4 * x2 + 4 * (x21 * x3) + 10 * (x23 * x25) + 5 * (x28 * x33) + 10 * (x28 * x5) - 8 * (x30 * x36) - 14067 ,
10 * (x0 * x26) + 6 * (x0 * x29) - 7 * (x13 * x29) + 8 * (x21 * x7) + 9 * (x22 * x25) - 8 * (x23 * x5) + 8 * (x26 * x32) + 5 * (x27 * x30) + 9 * (x27 * x31) + 6 * (x28 * x6) - 9 * (x29 * x5) - 4 * (x31 * x8) - 10 * (x32 * x35) + 10 * x35 * x35 - 55102 ,
3 * (x0 * x16) + 4 * (x1 * x36) + 8 * (x10 * x33) - 8 * (x12 * x17) - 8 * (x14 * x28) + 7 * (x15 * x25) - 2 * (x15 * x6) + 6 * (x15 * x8) - 2 * (x2 * x25) - 7 * (x2 * x34) + x23 * x35 - 5 * (x27 * x9) + 6 * (x28 * x30) + 6 * (x28 * x37) + 8 * (x28 * x7) - 4 * x30 + 7 * (x32 * x35) + 7 * (x35 * x5) + 7 * (x35 * x7) - 10 * (x5 * x7) - 2 * (x7 * x9) - 102697 ,
7 * (x0 * x27) + 3 * (x1 * x15) - 9 * (x1 * x29) - 3 * (x10 * x33) - 10 * (x12 * x34) - 8 * (x15 * x2) - 8 * (x18 * x23) - 6 * (x19 * x7) - 6 * (x2 * x34) + 7 * (x2 * x7) - 3 * (x20 * x22) - 8 * (x23 * x25) - 3 * (x26 * x34) - 9 * (x28 * x3) - 8 * (x28 * x35) + 3 * (x36 * x4) + 6 * x8 + 324145 ,
-9 * (x0 * x2) + 5 * x1 - 9 * (x13 * x3) + 4 * (x14 * x17) + 9 * (x18 * x29) + 5 * (x18 * x9) + 5 * (x20 * x23) - x20 * x5 - 8 * (x21 * x33) - 7 * x27 + 6 * (x28 * x7) - 7 * (x29 * x9) + 10 * (x31 * x6) + 52822 ,
-6 * (x10 * x29) - 2 * (x10 * x33) + 4 * (x11 * x31) + 8 * (x12 * x27) - 9 * (x12 * x36) + 2 * (x16 * x24) + 2 * (x19 * x34) - 8 * (x19 * x37) - 10 * (x24 * x7) - 5 * (x34 * x6) - 2 * (x7 * x8) + 9 * x9 + 119387 ,
6 * (x0 * x22) - 3 * (x12 * x37) - 3 * (x12 * x5) - 2 * (x13 * x36) - 10 * (x19 * x5) + 7 * (x2 * x22) + 7 * (x2 * x9) - 8 * x21 * x21 + x21 * x34 - 5 * (x23 * x26) + 9 * (x25 * x5) + 8 * (x25 * x9) + 4 * (x3 * x30) - 3 * (x37 * x7) - 6 * (x37 * x9) + 4832 ,
-2 * x0 * x0 + 3 * (x13 * x29) + x17 * x25 - 10 * (x21 * x28) + 5 * (x22 * x31) + 10 * (x22 * x9) - 10 * (x25 * x32) + 4 * x27 + 6 * (x29 * x6) - 4 * (x30 * x34) - 9 * (x31 * x4) + 2 * (x32 * x34) - 7 * (x4 * x6) + 123454 ,
4 * (x0 * x20) + x0 * x3 - 9 * (x1 * x17) + 9 * (x11 * x34) - 6 * (x13 * x7) - 6 * (x14 * x2) + 6 * (x14 * x29) + 7 * (x15 * x27) - 7 * (x18 * x5) - 7 * x20 * x20 + 8 * (x20 * x21) + 9 * (x20 * x27) + 2 * (x21 * x25) - 6 * (x25 * x28) - 9 * (x28 * x32) - 6 * (x3 * x32) - 3 * (x33 * x7) - 8 * (x36 * x9) + 170296 ,
6 * (x0 * x11) + x1 * x12 - 9 * (x1 * x30) - 10 * (x1 * x35) + 8 * (x10 * x7) + 5 * (x14 * x28) + 7 * (x16 * x21) - 10 * (x19 * x35) + x19 * x6 + 8 * (x2 * x31) - 2 * (x21 * x26) - 3 * (x23 * x27) + 9 * (x27 * x34) + 4 * x28 * x28 - x3 * x31 + x30 * x37 - 9 * (x30 * x4) + 4 * x34 - 76173 ,
-8 * (x0 * x15) - 4 * (x11 * x15) + 9 * (x12 * x23) - 10 * (x12 * x29) + 8 * (x13 * x26) + 6 * (x13 * x9) - x15 * x27 - x15 * x33 + 3 * (x19 * x29) - 10 * (x2 * x20) - x22 * x32 + 5 * (x23 * x8) + 6 * (x32 * x5) - 27078 ,
8 * (x1 * x9) + 8 * (x10 * x16) - 3 * (x10 * x29) - 2 * (x11 * x13) + 6 * (x11 * x33) + 3 * (x12 * x14) + 8 * (x12 * x16) + 5 * (x16 * x34) + 7 * (x18 * x32) + 8 * (x19 * x26) + 2 * x19 - 4 * (x20 * x6) + 4 * x22 * x22 - 8 * (x25 * x5) - 7 * (x26 * x34) - x29 + 10 * (x3 * x4) - 6 * x32 * x32 - 299677 ,
3 * (x0 * x6) + 7 * (x10 * x34) + 9 * (x11 * x18) - 8 * (x12 * x3) - x12 * x33 - x12 * x34 - 7 * (x16 * x7) + x16 * x8 - 3 * (x19 * x20) - 6 * (x19 * x33) - 8 * (x22 * x27) - 4 * (x24 * x3) + 57797 ,
9 * (x0 * x29) + 2 * (x1 * x19) + 8 * (x10 * x30) - 2 * (x11 * x20) - 6 * (x11 * x29) + 3 * (x13 * x20) - 10 * (x14 * x17) - 10 * (x15 * x19) + 6 * (x15 * x23) + 7 * (x15 * x4) + 6 * (x18 * x28) + x19 * x3 - x20 * x3 - 10 * (x21 * x30) + 10 * (x22 * x27) - 10 * (x23 * x31) + 2 * (x24 * x5) - 3 * (x25 * x31) + 5 * (x26 * x7) + 7 * x3 * x3 + 7 * (x30 * x32) + 6 * (x31 * x5) + 10 * x33 - 7 * x5 - 258015 ,
2 * (x0 * x16) - 6 * (x1 * x20) + 5 * (x10 * x17) - 5 * (x15 * x23) + 8 * (x16 * x18) + 9 * (x19 * x36) + 6 * (x2 * x33) - 9 * (x23 * x9) + 9 * x25 * x25 + 2 * (x3 * x37) + 7 * (x30 * x34) - 2 * x32 - 157310 ,
-3 * (x0 * x25) - 2 * (x1 * x36) + 2 * (x10 * x31) + 9 * (x13 * x20) - 5 * (x15 * x2) - 6 * (x15 * x37) - 2 * x17 + 8 * (x19 * x28) + 7 * (x2 * x32) - 2 * (x21 * x30) + 5 * (x23 * x5) + 5 * (x24 * x26) - 8 * (x24 * x33) - 8 * (x26 * x35) - 10 * x26 - 10 * (x29 * x36) - 2 * (x30 * x6) + 4 * (x31 * x36) + 9 * (x33 * x9) - x37 * x6 + 7350 ,
-8 * (x0 * x36) - 8 * (x17 * x32) + 8 * (x2 * x33) - 7 * (x22 * x28) - 9 * (x22 * x35) + 8 * (x22 * x5) - 2 * (x23 * x5) + 5 * (x26 * x27) + 6 * (x26 * x31) - 3 * (x32 * x33) - 2 * (x35 * x4) + x36 * x8 + 85362 ,
7 * (x0 * x33) - 5 * (x12 * x35) + x12 * x9 + 10 * (x13 * x30) + 8 * (x15 * x32) - 9 * (x2 * x20) + 3 * (x2 * x30) + 10 * (x25 * x29) - 6 * (x26 * x32) - 3 * (x27 * x9) + 7 * (x36 * x6) - 121182 ,
8 * (x0 * x17) + 10 * (x1 * x14) + 2 * (x10 * x33) + 8 * (x13 * x26) - 5 * (x14 * x34) - 9 * (x14 * x7) + x18 * x2 - 10 * (x18 * x7) + x2 * x33 + 10 * x20 - 6 * (x22 * x30) + 6 * (x22 * x9) + 10 * (x23 * x34) + 9 * (x25 * x9) + 7 * (x26 * x30) - 9 * (x27 * x31) + 7 * (x28 * x5) - 8 * (x30 * x31) - 9 * x34 * x34 + 2 * (x36 * x8) - 136304 ,
-4 * (x0 * x25) - 9 * (x1 * x21) - 9 * (x1 * x25) + 6 * (x12 * x5) + 6 * (x2 * x28) - 4 * (x20 * x28) - 8 * (x22 * x23) + 5 * (x23 * x32) - 6 * (x24 * x28) - 6 * (x25 * x29) + 121526 ,
-4 * (x0 * x30) + x11 * x14 - 6 * (x12 * x20) - 8 * (x13 * x28) + 10 * (x15 * x2) - 10 * (x18 * x25) + 6 * (x22 * x29) - 3 * (x25 * x8) + x27 * x36 - 2 * (x3 * x30) + 10 * (x30 * x34) + 4 * (x35 * x6) - 27523 ,
-9 * (x10 * x30) - 3 * (x10 * x6) - 10 * (x13 * x29) - 8 * (x13 * x7) + 3 * (x14 * x32) - 2 * (x18 * x20) + 10 * (x18 * x34) - 4 * (x2 * x7) + 9 * (x20 * x22) - 5 * (x20 * x33) - 10 * (x23 * x34) - 6 * x26 + 2 * (x3 * x34) + 9 * x30 * x30 + 8 * (x31 * x8) + 9 * (x33 * x36) + 35830 ,
7 * (x10 * x2) + 2 * x10 - 5 * (x13 * x9) + 10 * (x15 * x33) + 8 * (x17 * x23) + 5 * x2 * x2 - 8 * (x2 * x37) + 6 * (x20 * x24) + 4 * (x20 * x35) - 8 * (x23 * x8) - 9 * (x24 * x7) + 7 * (x26 * x8) - 5 * (x3 * x36) + 6 * (x30 * x35) - 7 * x36 - 5 * x7 - 59235 ,
-8 * x11 * x11 - 9 * (x14 * x31) - 8 * (x14 * x35) + 7 * (x15 * x20) + x15 * x24 + 6 * (x15 * x25) - 10 * (x16 * x18) - x16 * x9 + 8 * (x19 * x32) + 5 * (x2 * x5) + 6 * (x21 * x30) - 10 * (x22 * x24) + 2 * (x22 * x34) - 10 * (x22 * x37) + 4 * (x27 * x35) - x28 * x33 + 2 * (x28 * x37) + 7 * (x29 * x37) - 2 * (x34 * x35) - 7 * (x35 * x6) + 82407 ,
7 * (x0 * x27) + 7 * (x10 * x21) - 10 * (x10 * x3) + 6 * (x13 * x36) - 3 * (x15 * x17) + 7 * (x15 * x30) - x15 * x7 + x16 * x34 + 8 * (x17 * x37) + 2 * x2 + 6 * (x20 * x21) + 9 * (x20 * x33) + 8 * (x20 * x4) + 3 * (x21 * x25) + x22 * x28 + 6 * x23 * x23 - 6 * (x24 * x3) + 10 * (x25 * x27) + 5 * (x29 * x4) - 6 * (x3 * x32) - 6 * (x30 * x4) - 5 * (x30 * x5) - x33 * x34 - 7 * (x4 * x9) - 4 * (x7 * x9) - 154206 ,
2 * x0 * x0 + 2 * (x0 * x14) + 7 * (x11 * x13) - 9 * (x11 * x16) + 2 * (x11 * x21) + 8 * (x11 * x24) + 5 * (x11 * x4) + 4 * (x13 * x36) - 8 * (x15 * x16) - 4 * (x16 * x17) - 3 * (x16 * x23) - 8 * (x17 * x33) - 4 * (x17 * x34) - 6 * (x18 * x31) + 7 * (x2 * x25) - x20 * x25 + 5 * (x20 * x9) + 2 * (x21 * x26) - 5 * (x21 * x5) + 4 * (x22 * x35) - 7 * (x23 * x9) - 10 * (x31 * x7) + 156020 ,
-5 * (x12 * x34) + 4 * (x12 * x9) - 2 * (x13 * x31) + x14 * x9 + 4 * (x17 * x32) - 2 * (x18 * x23) - 10 * (x18 * x29) + 6 * (x19 * x30) + 4 * (x2 * x32) - 9 * x27 * x27 - 2 * (x3 * x35) - 2 * (x3 * x5) - 2 * (x7 * x8) + 129397 ,
-9 * x1 + 5 * (x12 * x2) + 4 * (x12 * x35) - 5 * (x14 * x8) + 2 * x15 + 3 * (x17 * x22) - 3 * (x17 * x23) + 9 * (x18 * x33) - 5 * (x20 * x23) - 8 * (x20 * x34) - 8 * (x29 * x6) + 70585 ,
x0 * x1 + 6 * (x0 * x12) + 10 * (x10 * x31) + 8 * (x11 * x32) + 9 * (x13 * x14) - 2 * (x15 * x33) - 9 * (x15 * x9) + 4 * (x16 * x9) - 2 * (x18 * x29) - 5 * (x2 * x36) + 2 * (x21 * x32) - 8 * (x24 * x33) + 9 * (x25 * x26) + x26 * x28 - x26 * x3 - 3 * (x26 * x6) + 6 * x29 - 2 * (x37 * x7) - 119430 ,
x0 * x2 + 10 * x10 + 6 * (x12 * x18) - 5 * (x12 * x35) + 9 * (x13 * x29) - 2 * (x14 * x37) + 10 * (x15 * x23) + 7 * (x15 * x4) - 5 * (x16 * x9) - 9 * (x20 * x8) - 4 * (x21 * x27) - 5 * (x22 * x5) + x28 * x6 + x3 * x36 + 8 * (x33 * x35) - 144386 ,
-5 * (x1 * x12) + 4 * (x1 * x6) + 4 * (x11 * x5) + 8 * (x15 * x20) + 7 * (x15 * x22) - 10 * (x19 * x29) - 6 * x2 * x2 + 5 * (x2 * x31) - 2 * (x2 * x9) + 2 * (x20 * x35) + 7 * (x29 * x5) + 8 * (x30 * x7) + 8 * (x35 * x4) - 2 * x37 * x37 - 99154 ,
-2 * x0 * x0 + 5 * (x0 * x11) - 10 * (x0 * x21) + 9 * (x0 * x30) - 2 * (x1 * x29) + 6 * (x10 * x29) - 9 * (x10 * x30) - 8 * (x10 * x32) + 9 * x11 * x11 - 9 * (x11 * x5) - x13 * x17 + 5 * (x13 * x6) + 9 * (x14 * x20) - 10 * x18 * x18 - 5 * (x19 * x24) + 7 * (x2 * x26) + 10 * (x20 * x21) - 9 * (x24 * x34) - 5 * (x24 * x5) - 9 * (x26 * x32) - 6 * (x30 * x7) - 7 * (x32 * x37) + 414339 ,
2 * (x0 * x21) - 10 * (x0 * x35) + 9 * (x11 * x15) - 2 * (x12 * x4) + 4 * (x16 * x4) + 2 * (x17 * x32) - 8 * (x2 * x20) + 10 * (x21 * x23) + 2 * (x21 * x27) - 5 * (x21 * x30) + 8 * (x22 * x30) + 2 * (x25 * x4) + 9 * (x28 * x34) + 3 * (x30 * x5) + 4 * (x33 * x7) - 3 * (x6 * x8) - 169458 ,
x10 * x31 - 4 * (x10 * x4) - x11 * x22 - 10 * (x12 * x5) - 4 * (x16 * x19) + 3 * (x19 * x2) + 3 * (x19 * x34) - 6 * x19 + 4 * (x2 * x32) - 8 * (x22 * x33) + 8 * x23 * x23 + 2 * (x24 * x6) + 8 * x31 + 2 * (x5 * x7) - 26425 ,
8 * (x1 * x35) - 3 * (x1 * x7) - 3 * (x14 * x23) - 6 * (x16 * x28) - 2 * (x16 * x6) - 7 * x16 + 4 * (x2 * x4) + x21 * x24 - 5 * (x23 * x3) - 9 * (x24 * x30) + 9 * (x26 * x35) - 8 * (x28 * x4) - 9 * (x3 * x32) + 2 * x3 + 209624 ,
-10 * (x0 * x28) + 2 * (x0 * x3) + 8 * (x10 * x30) - x11 * x31 + 6 * (x13 * x32) + 10 * (x14 * x36) + 5 * (x15 * x23) + 2 * (x15 * x31) + 2 * (x16 * x25) + 10 * (x16 * x30) - 10 * (x18 * x22) + 8 * (x19 * x6) - 7 * (x2 * x36) - x21 * x29 - 4 * (x24 * x4) + 8 * (x26 * x5) + 10 * (x31 * x5) - 5 * (x32 * x7) - 4 * (x36 * x5) - 146637 ,
-2 * (x1 * x23) + 9 * (x10 * x9) + 9 * (x15 * x21) + 10 * (x16 * x25) + 5 * (x16 * x36) + 7 * (x16 * x6) + 7 * (x18 * x35) + 8 * (x19 * x3) - 9 * (x19 * x35) + 10 * (x2 * x32) + 5 * (x2 * x4) - x21 * x27 - 6 * (x24 * x35) - 3 * (x25 * x26) + 6 * (x29 * x36) + 6 * (x29 * x4) - 3 * (x33 * x4) - 5 * (x34 * x5) - 3 * (x37 * x7) + 9 * (x4 * x8) - 422738 ,
]
remaining_vars = [v for v in x if v not in known]
simplified = [eq.subs(known) for eq in eqs]
def objective(vars):
values = dict(zip(remaining_vars, vars))
return [float(eq.subs(values)) for eq in simplified]
sol = least_squares(objective, [100]*len(remaining_vars), method='lm')
flag = []
for i in range(38):
val = known.get(x[i], sol.x[remaining_vars.index(x[i])] if x[i] in remaining_vars else 0)
flag.append(chr(max(32, min(126, int(round(val))))))
print("Possible flag:", ''.join(flag))
solve_flag()
|