软件系统安全赛Writeup+赛后复现
软件系统安全赛Writeup+赛后复现
5G消息
CTF-NetA分析流量包,其解析tls流量需要tls.keylog文件
tcp流中存在明文
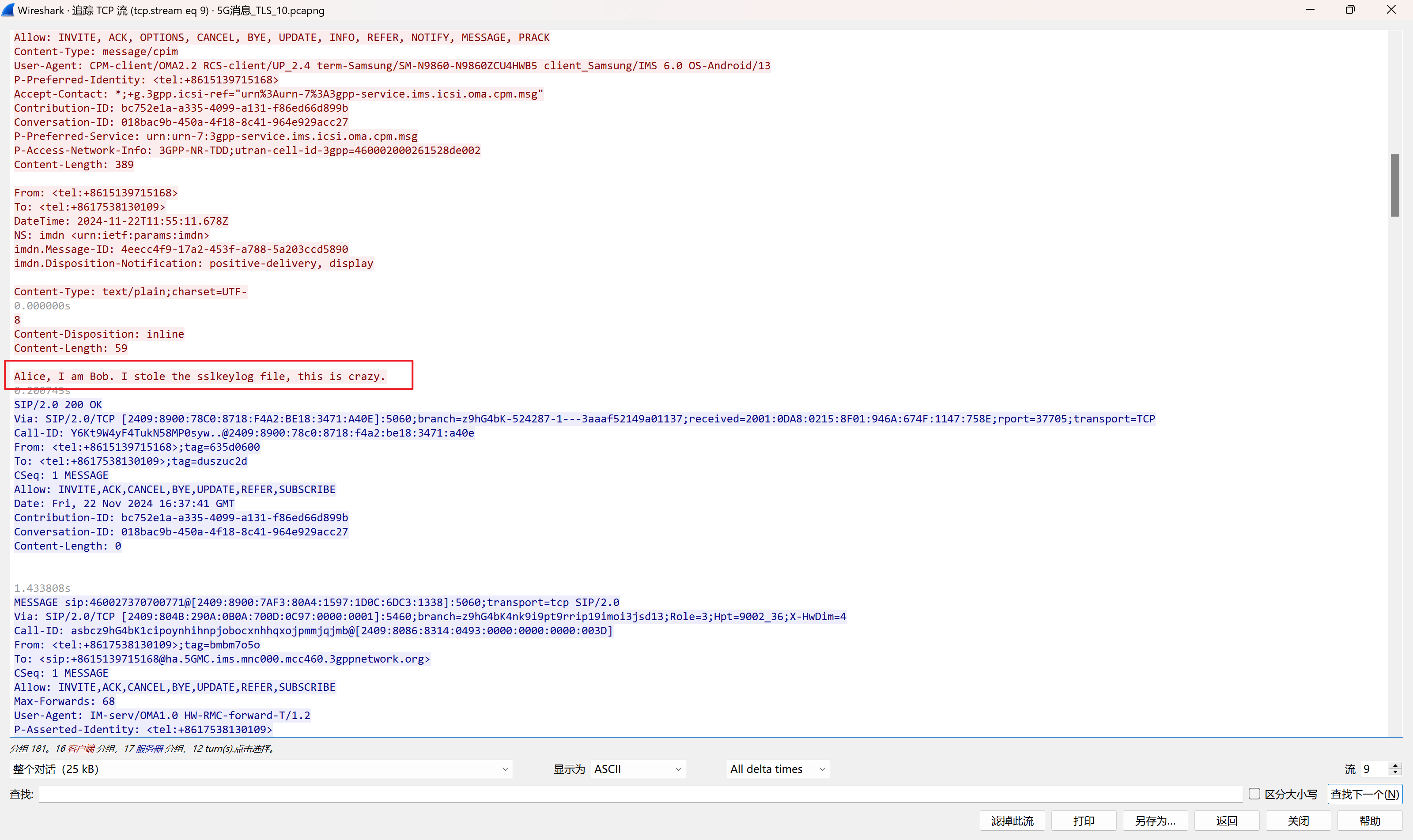
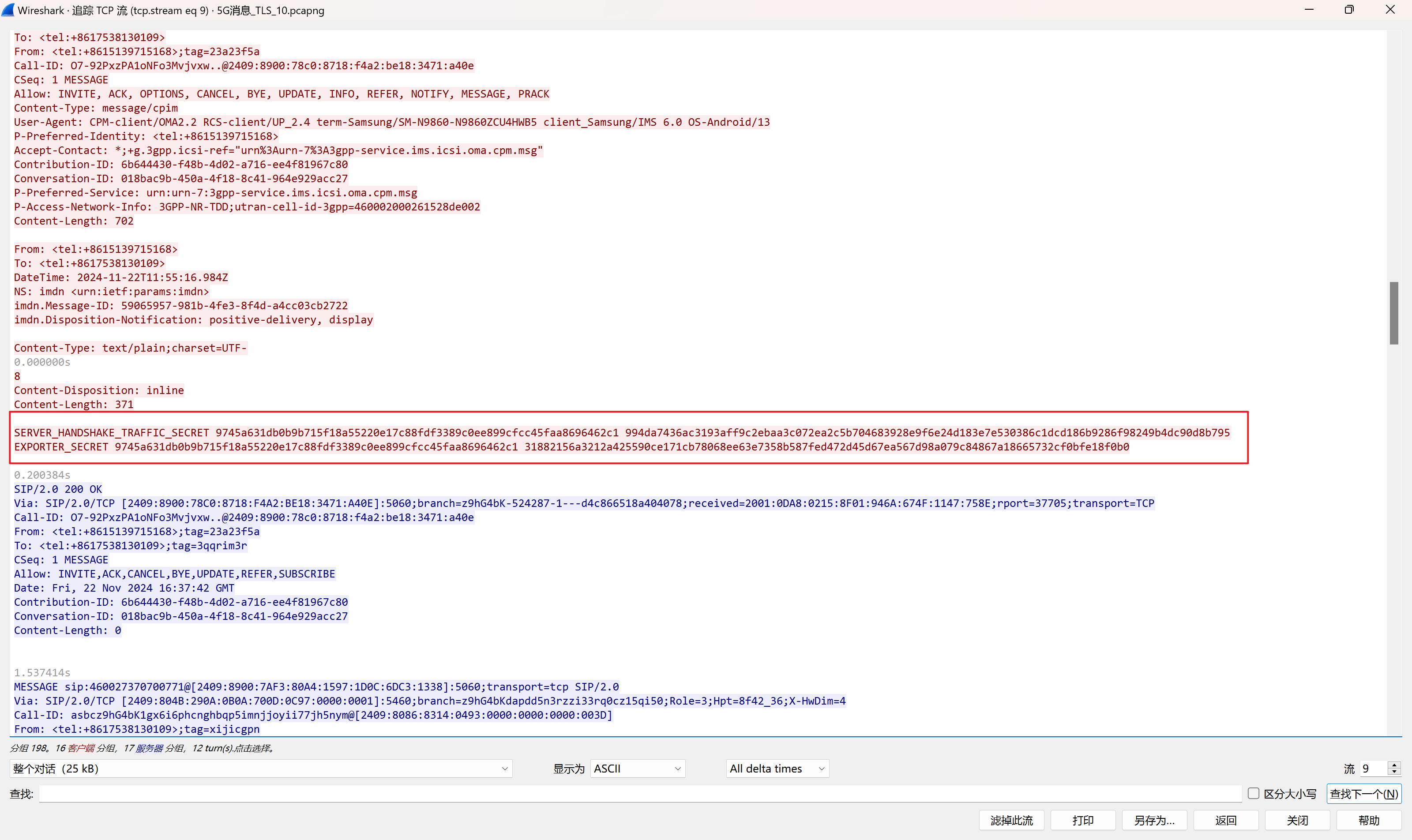
多条流量中包含了keylog的内容
几段内容拼接后内容为:
1 | |
重新分析tls流量
发现存在png信息
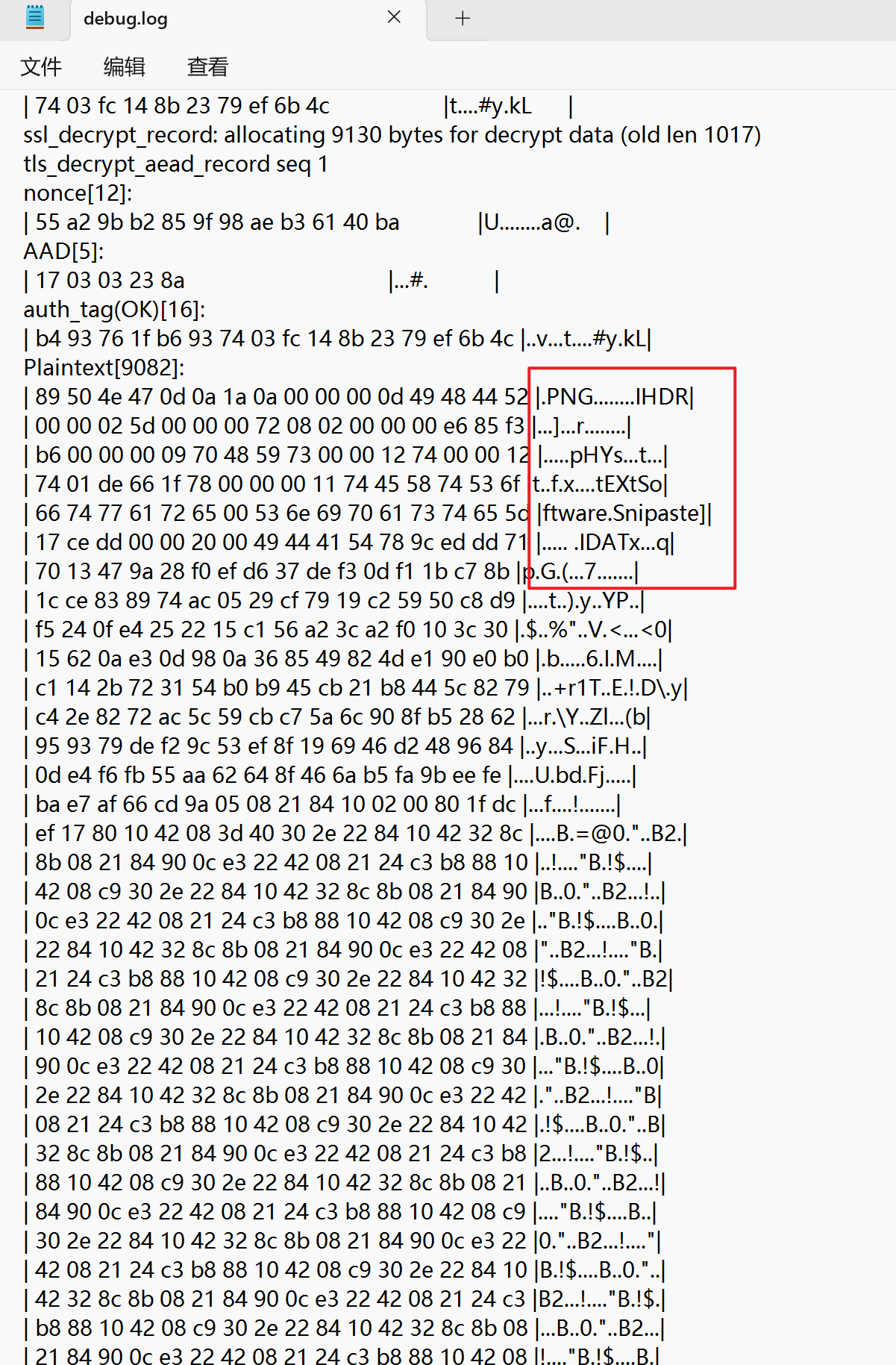
数据保存为图片
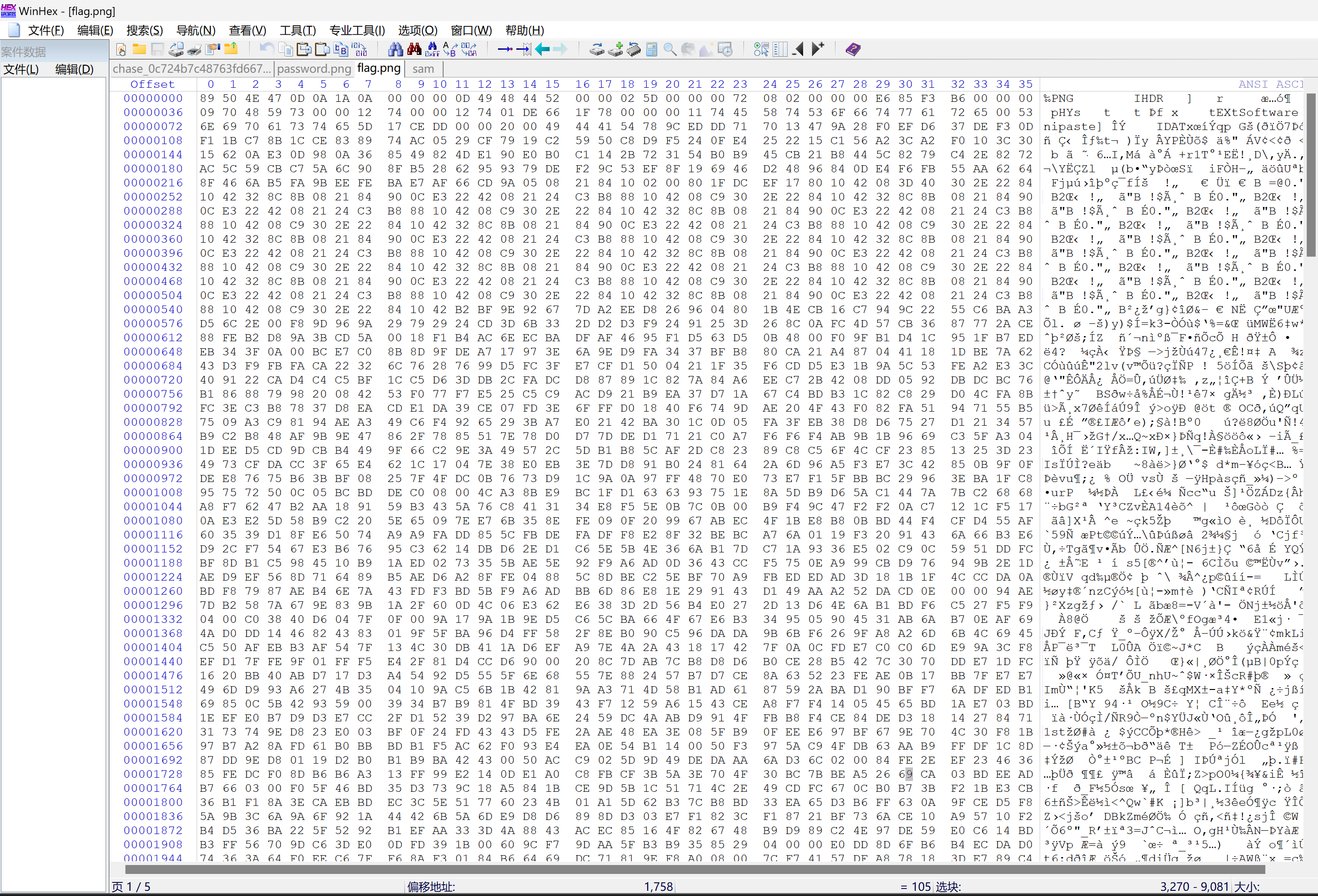
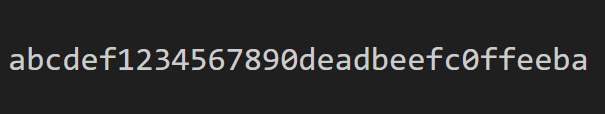
得到flag:abcdef1234567890deadbeefc0ffeeba
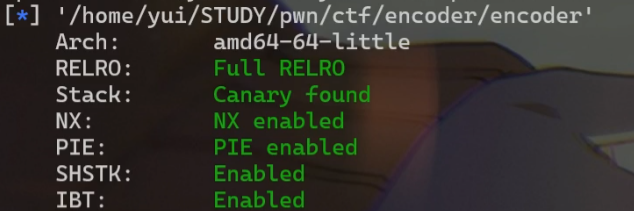
encoder-攻击
64位,保护全开
菜单题,实现了一个简单的文件管理系统,有以下功能:
- upload
- download
- encode
- decode
- release
encode使用RLE算法对文件进行编码,在编码数据前添加头部信息:“RLE\n”、编码后长度、校验和
1 | |
decode函数用于解码encode函数编码后的文件,仅对头部进行检验,我们可以通过伪造头部信息,来覆盖相邻的堆块大小,再利用release函数即可实现泄露libc和free_hook
利用过程
malloc一个伪造的块,用于溢出覆盖相邻堆大小,再malloc几个小块,decode伪造块修改大小后,即可利用unsortedbin attack泄露libc
修改fd指针为__free_hook-0x8,后续分配会写在__free_hook-0x8的位置,即可实现修改__free_hook为system,劫持__free_hook触发shell
exp
1 | |

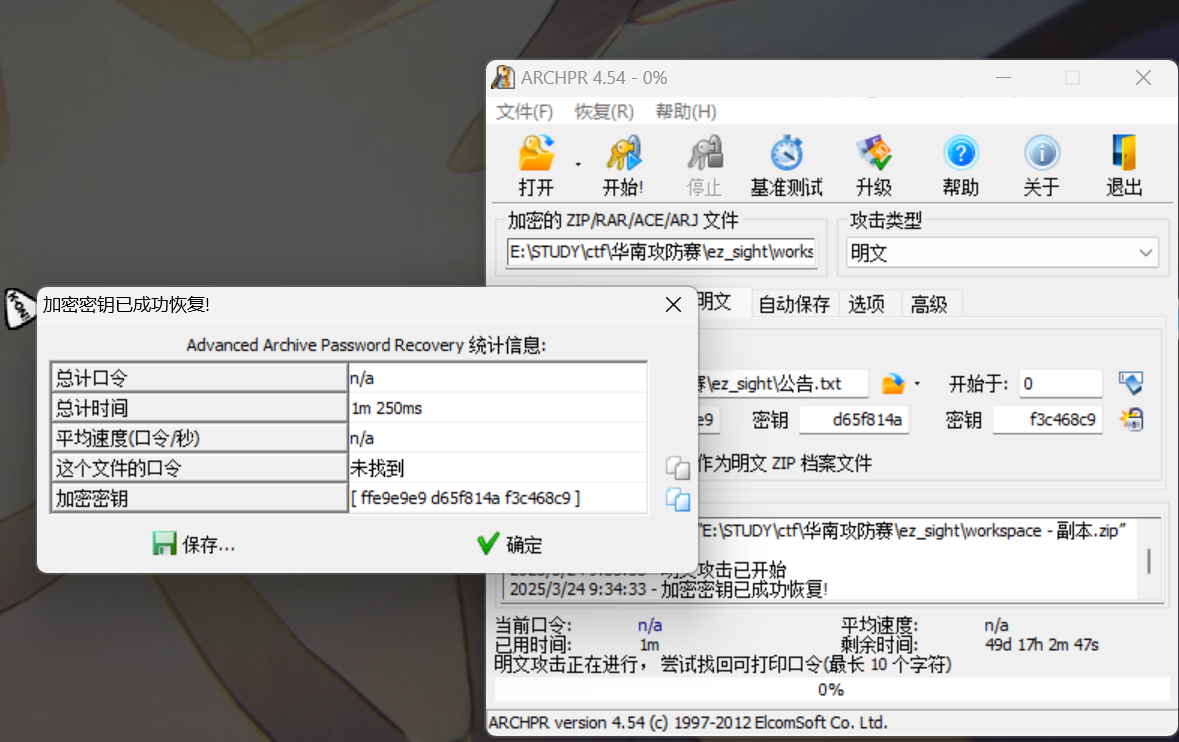
ez_sight
明文攻击解压缩包
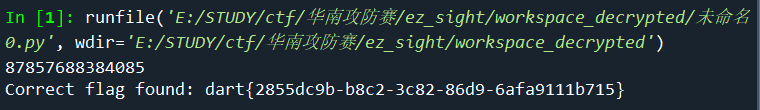
使用给的password.pt模型对图片进行预测
1 | |
取每个位置概率最高的几个数字爆破
1 | |
得解
软件系统安全赛Writeup+赛后复现
https://xu17.top/2025/03/25/软件系统安全赛现场赛Writeup/